Issuing eID Certificates and Signing ePassports
PrimeKey has over 20 years of experience in issuing certificates for tokens and cards for both X509 and Card Verifiable Certificates (CVC), and EJBCA PKI together with PrimeKey's SignServer form the technology base of many passport authorities worldwide.
ePassport Concepts
Modern passports are no longer only authenticated visually but also contain an RFID chip to protect an otherwise authentic passport from modification. Two basic mechanisms currently exist for protecting the integrity of a passport
:
Machine Readable Travel Documents (MRTD) - Basic Access Control (BAC): MRTD PKI is needed for all ePassport and is used in the process to sign the electronic data stored in an ePassport.
Extended Access Control (EAC): EAC PKI is needed for EU EAC ePassport and is used in the EU to protect fingerprints and iris stored in an ePassport.
MRTD PKI is specified in the International Civil Aviation Organizati on ( ICAO ) sta ndard ICAO 9303, while EAC is an EU-specific specification.
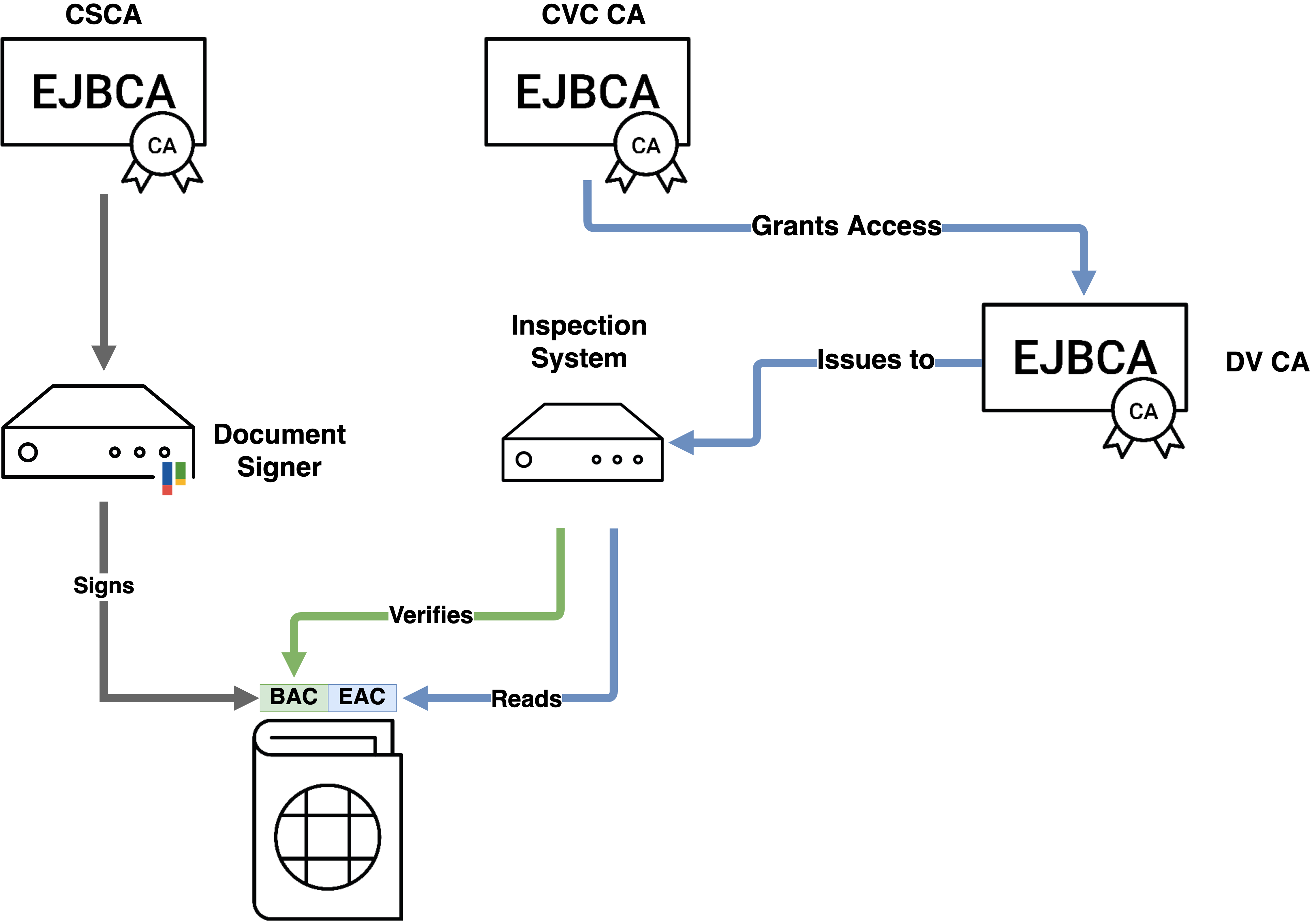
MRTD - Basic Access Control (BAC)
As defined by ICAO, Basic Access Control (BAC) allows a reader to read the basic data contained in the RFID chip of an ePassport (name, passport number, photograph, etc) to guard against fraud by physically altering the passport. To verify the validity of the data on the chip it also contains a digital signature issued by a Document Signer (for example PrimeKey SignServer), whose certificate is issued by a Country Signing Certificate Authority (CSCA) hosted by the issuing country. The CSCA and Document Signer certificates are basic X509 certificates, and the public key lists required to verify can either be physically exchanged or downloaded from a central master list, while a National Public Key Directory (NPKD) allows for the easy exchange of keys and CRLs. As part of the complete solution, PrimeKey also offers an NPKD implementation, designed to manage certificates for ePassports in compliance with International Civil Aviation Organization ( ICAO ) standards.
Extended Access Control (EAC)
An extension of BAC, Extended Access Control also allows the passport to store biometric data such as fingerprints and iris/retinal scans. In order for partnering countries to authorize and control access to this data, each country needs to establish a CVC CA, that in contrary to the CSCA is based on the Card Verifiable Certificate (CVC) standard. To enable access, each country then needs to create a Document Verifier CA (DVCA), which is a Sub CA signed by the partnering country's CVCA. The DVCA can then issue certificates to Inspection Systems (IS) which are in turn authorized to read the protected fields in the ePassport's RFID chip. To facilitate the creation of Inspection Systems between countries, a Single Point of Contact (SPOC) is used.
Set up and Configure CSCA
Setting up a Country Signing Certificate Authority (CSCA) includes creating a new self signed root CA in EJBCA and creating a Certificate Profile compliant with CSCA certificates.
Set up Certificate Profiles
Certificate Profiles for passport signers are issued by the CSCA.
Set up and Configure BAC/EAC
Create Document Verifier CA
The DVCA is a Sub CA to the CVC CA and can either be created in your own PKI or imported from the associated country's PKI.
→ How to create a DV CA and enroll an Inspection System (IS)
Related Content
For a deep dive into the inner workings of EJBCA, see the EJBCA CA Concept Guide and for more information on setting up CAs, profiles, and general configuration of an EJBCA instance, see the EJBCA CA Operations Guide.
To find out more about other interesting solution areas and what you need to set up, see Solution Areas.