Hybrid PKI Deployment for Modern Manufacturers
As organizations strive to facilitate the management of their PKI it is common to perform PKI consolidation and migrate several disparate PKIs into a single multi-tenant PKI solution (such as EJBCA). Another trend in this area is using PKI as a Service (PKIaaS).
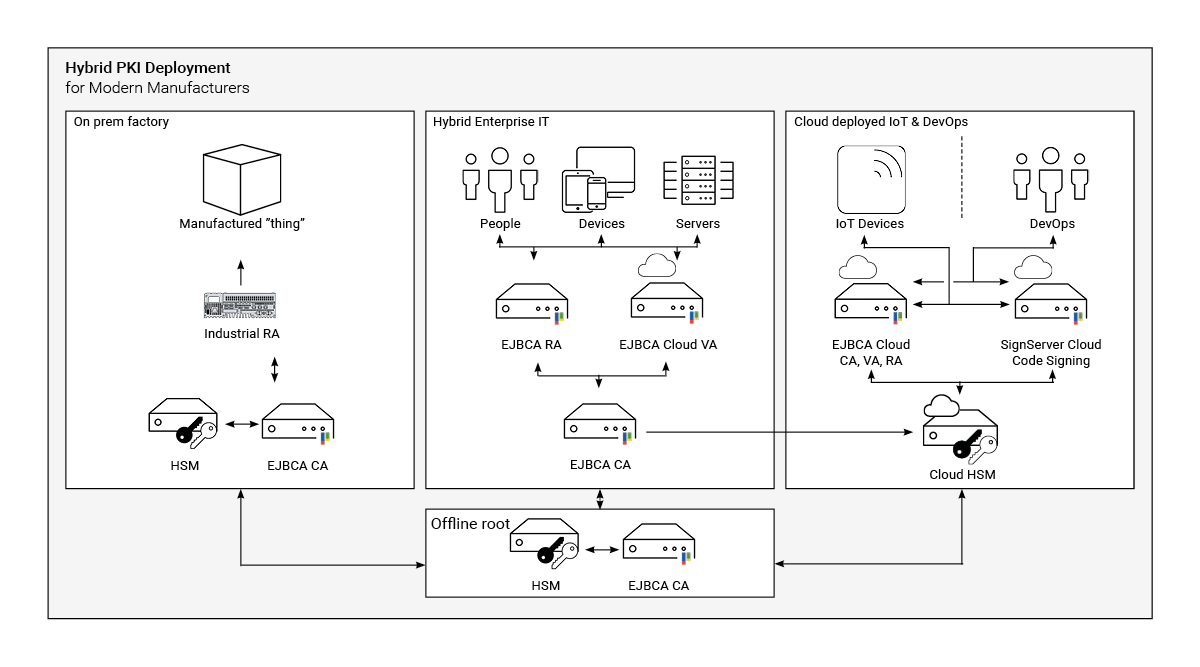
Even though PKI consolidation and PKISaaS are gaining popularity and it's easy to believe either is a one-stop-shop, the reality is that large organizations will continue to have several PKI silos. For bad and sometimes for good, PKI silos occur everywhere.
One situation when a silo may be beneficial is when requirements are so specific for an environment that the demands are incompatible with other PKI systems and could cause unwanted security or uptime risks to another system in a consolidated PKI. For example, very strict latency requirements are often hard to fulfill in a multi-use case environment, offline requirements where connectivity is not always available, or the need to process requests from high-risk clients or in higher-risk environments. The following outlines practical examples of PKI silos in a large organization:
A consolidated Enterprise PKI in the headquarter that serves many remote branches of the organization.
Multiple offices in remote locations need their own local PKI for practical or political reasons.
A new PKI for IoT devices.
Factories that need time-critical access and are not 100% online, new secure product lines requiring OT/IT integration.
DevOps workflows supporting enhanced software supply chain security, in need of fast PKI changes and rapidly changing integrations.
Specific business applications with PKI requirements that are so different from others that it’s motivated with a separate environment.
PKI silos can cause a loss of control over policy and operations or in other words a governance risk for something that may be a critical asset to the organization, not to mention the need for distributed PKI and HSM competence. The solution is to support silos and do so with a common technology and governance platform. If you standardize and streamline policy and operations across multiple silos, you gain back governance and minimize maintenance and risks. You also get the possibility to deploy PKIs in test and production environments with a high degree of automation.
Three components are key to maintaining central PKI governance and upholding control and security policy across the whole organization:
Consolidate PKIs into a common multi-tenant PKI where possible, see Migrating from other CAs to EJBCA.
Automate installation and configuration of PKI deployments and enable centrally controlled policy and profiles to be deployed anywhere, see Running PKI and Signature Services in DevOps Environments.
Consolidate HSM usage into a set of HSM platforms that functions the same, or similar enough, in all silos, regardless of whether it is on-premises or in the cloud.
Automating deployment, software provisioning, and configuration management tools enables you to easily deploy the PKI platform, HSM drivers, and configure HSM access from the PKI installation, even using different types of HSMs. Standardizing HSM usage across all deployments makes PKI governance much easier as you can leverage expertise across the organization. This enables one technology and one set of automated provisioning playbooks to be used across all PKI silos. No need for specialized competence in certain silos.
A technology platform that fully supports hybrid operation allows you to consolidate what can be consolidated, deploy PKI securely to all necessary silos, and rapidly provision new PKIs (in the consolidated platform or as a silo) when new business cases require. Such a hybrid deployment provides a joint platform with competence within the organization, without dependence on a few local specialists or insecure ad-hoc deployments.
HSMs as a Hybrid Combination
Using HSMs in a hybrid combination enables your organization to use the same HSM technology both on-premises and in the cloud.
For example, Thales offers a hybrid approach with the on-premises Luna HSMs and cloud-based Data Protection on Demand (DPoD). For more information on how to integrate EJBCA with Thales, see Thales Luna HSM and Thales DPoD .
Related Content
To find out more about other interesting solution areas and what you need to set up, see Solution Areas.
To learn more about how to integrate EJBCA, see EJBCA Integration and for even more guides, see Tutorials and Guides.