Securing Your Microsoft Environment with EJBCA
The Microsoft platform is one of the most prominent Enterprise environments globally, serving both servers and workstations. But while the Microsoft ecosystem is truly as mature as it is ubiquitous, Microsoft's own PKI, Microsoft Active Directory Certificate Services (AD CS), does not always grow in scale with your solution. You can solve that by leveraging EJBCA as the PKI backend instead of the Microsoft Certificate Authority (CA). Not only do you gain the power of one of the worlds best PKI tools in your environment, but you can save both cost and work by having a single EJBCA instance handle the entire PKI of your organization across all forests, domains, and trees, instead of having to maintain a separate Microsoft CA per domain.
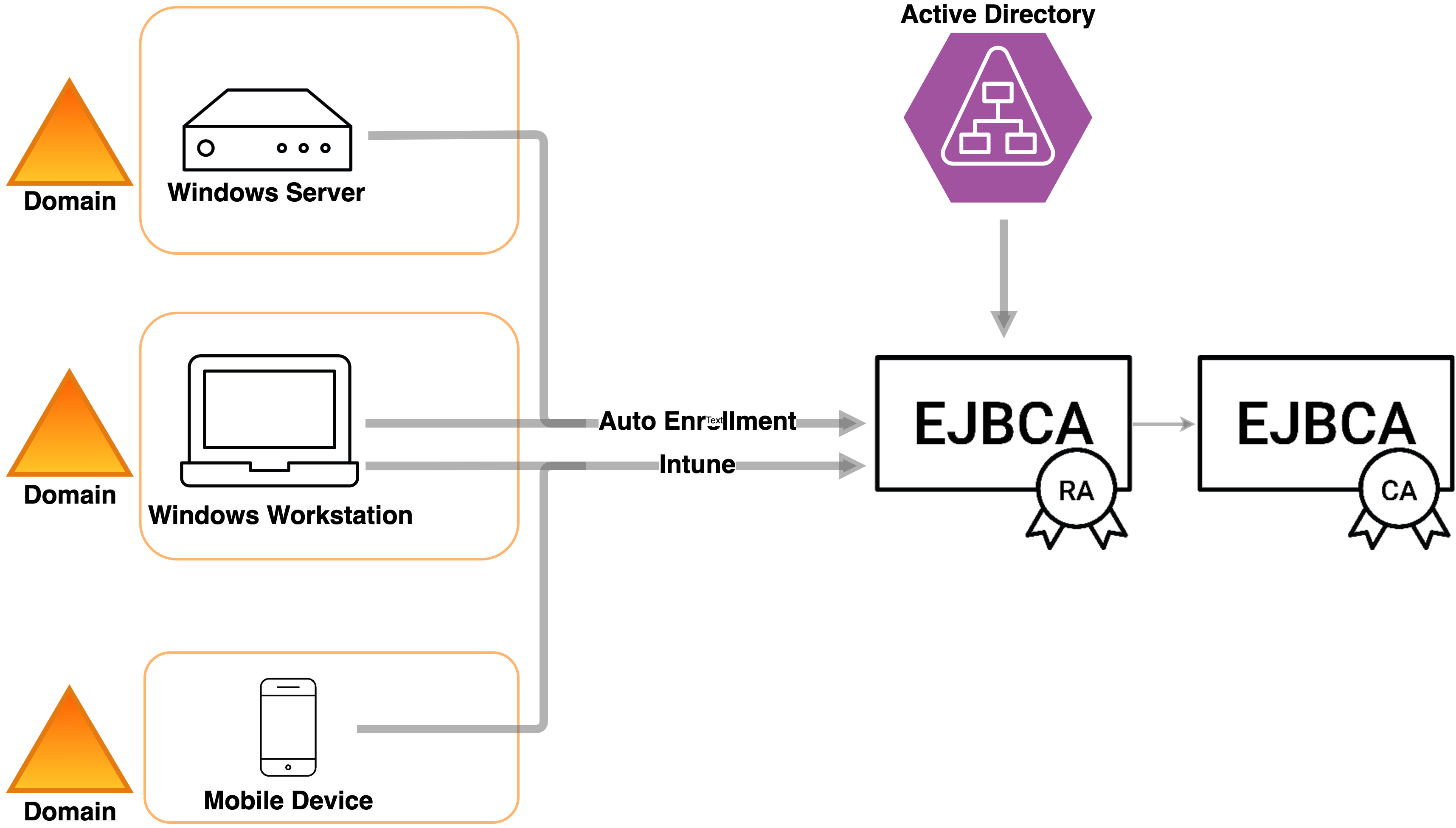
With EJBCA's Auto-enrollment functionality your clients user experience does not change, while your administrators will be overjoyed. Employing EJBCA as the CA backend for your Microsoft environment does away with the need for a Microsoft CA and Microsoft Certificate Services. Read on to learn how EJBCA integrates into your infrastructure via Microsoft Auto-enrollment and support for Intune and HSMs.
Microsoft Auto-enrollment
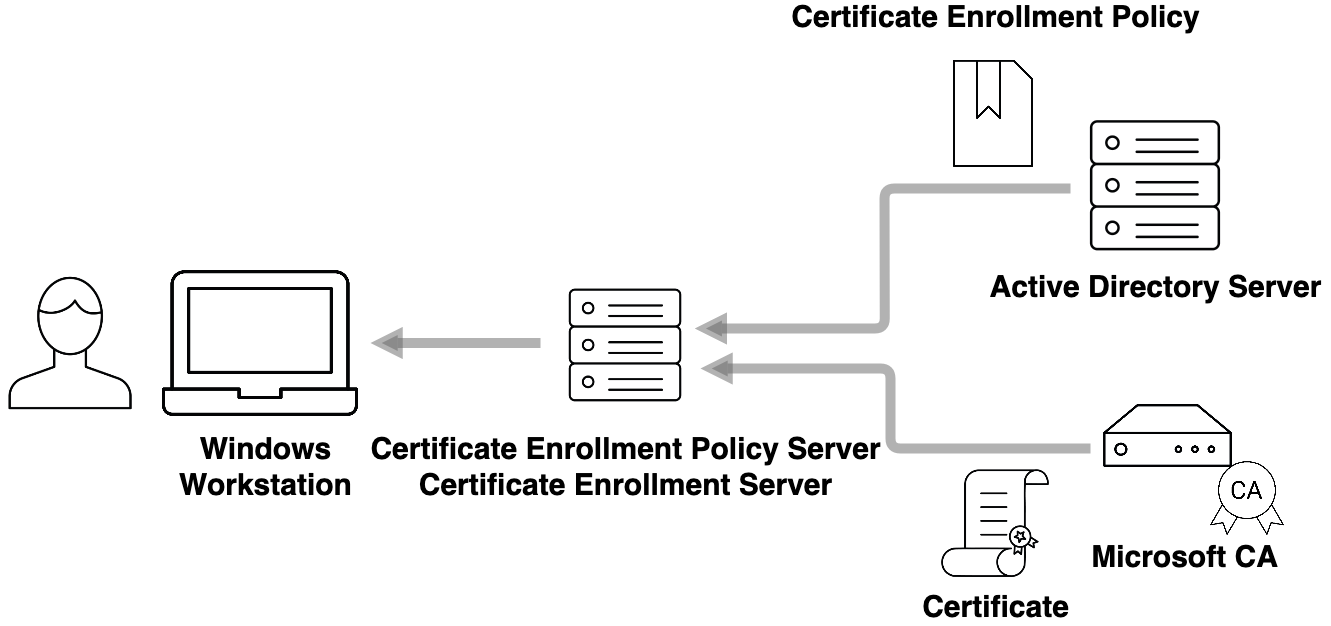
PKI is an integral part of any Windows environment. Servers, workstations, and mobile devices are managed through Active Directory (AD), defining domains and access for users and machines. Backing this is the built-in Microsoft CA, which checks with AD running on a Domain Controller.
When a client running Windows logs into a domain, it makes a request to a Certificate Enrollment Policy Web Service (CEP) to retrieve from the AD what policies the user is entitled to. A request is then sent through a Certificate Enrollment Web Service (CES) to request certificates from the Microsoft CA, which in turn gives access to the needed domains. This process is called Microsoft auto-enrollment and it works so well that you are not even aware that it's happening.
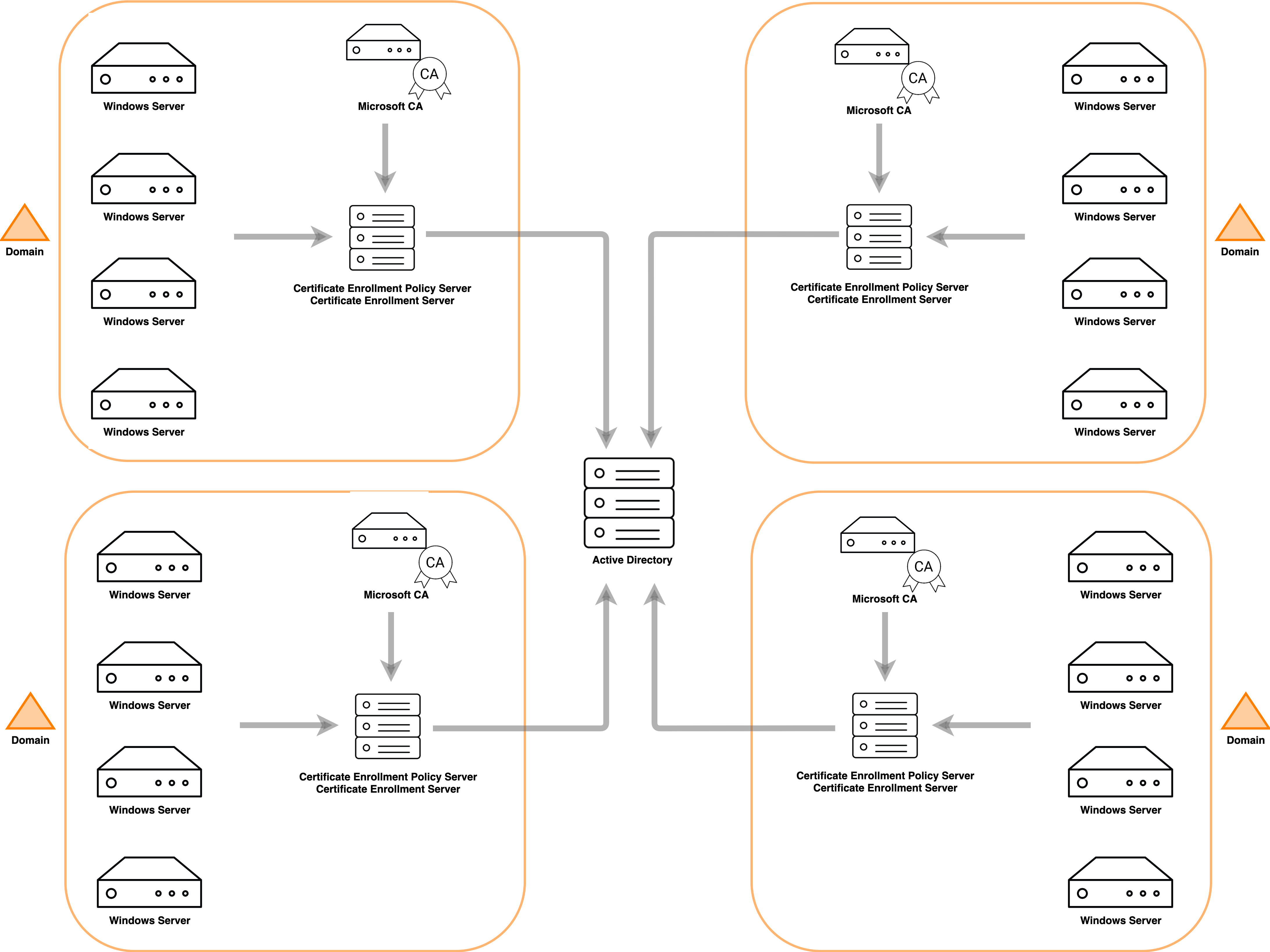
While this solution works well in small-scale environments, once multiple domains and forests need to be taken into consideration it scales poorly, requiring an equal number of CEP and CES servers and Microsoft CA instances to the number of domains.
EJBCA solves this problem by becoming a single source for all your enrollment needs.
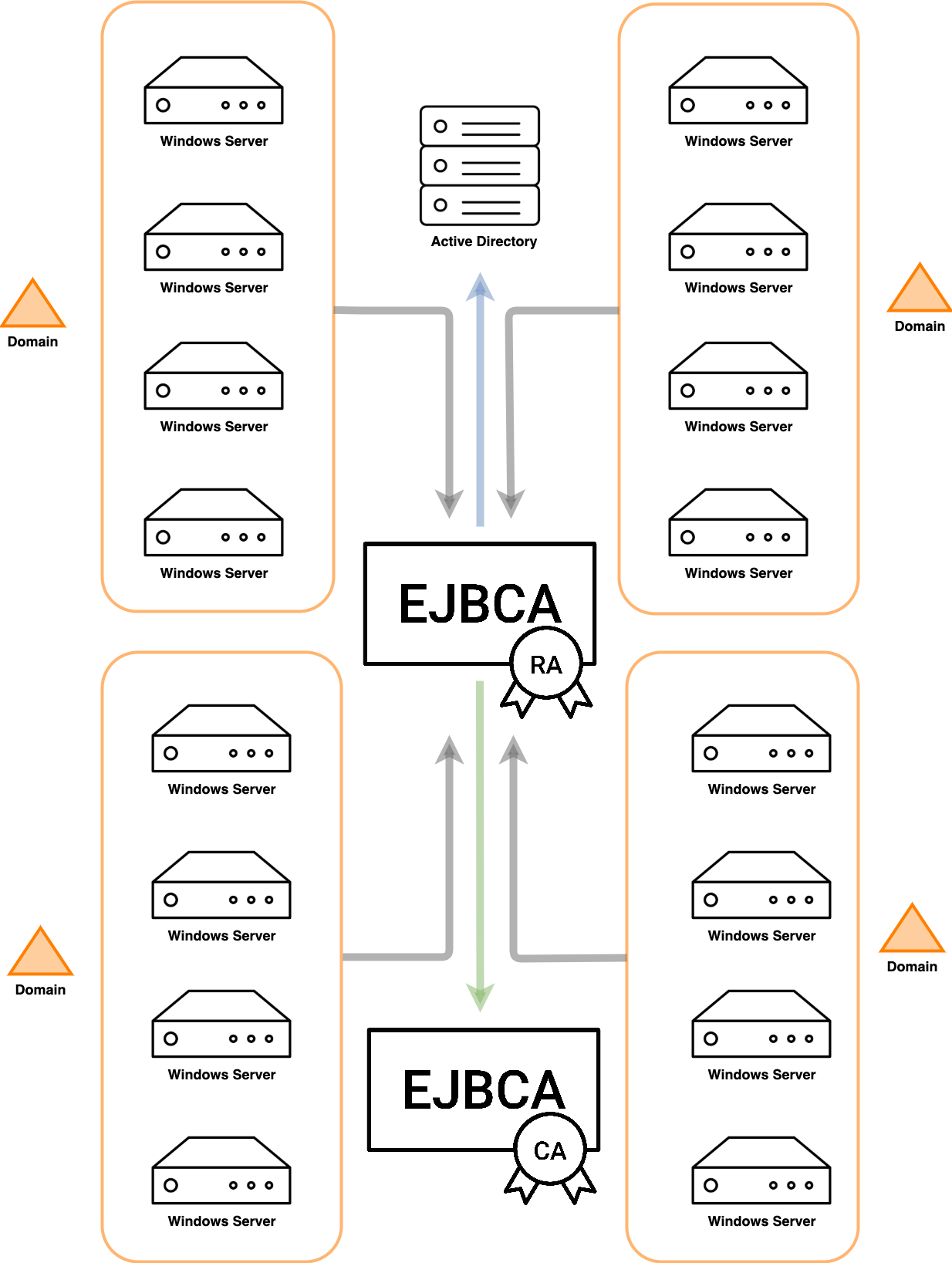
EJBCA’s MS Auto-enrollment support is built on the Certificate Enrollment Policy Protocol (XCEP) and WS-Trust Token Enrollment Extensions (WSTEP) enrollment stack which removes the need for a separate CEP or CES server to act as endpoints and does not require a separate Domain Controller per domain. Instead, the EJBCA RA is configured on the client as the enrollment endpoint and connects directly to Microsoft Active Directory to transmit the entitled Certificate Enrollment Policies to the client, then facilitates the actual enrollment with the EJBCA CA.
Configure your Microsoft Environment to Enroll against EJBCA
EJBCA's Microsoft Auto-enrollment support eliminates the need for a separate CEP or CES server, with the EJBCA RA as the point of first contact for enrolling clients. Once set up, EJBCA essentially fully replaces Microsoft's own CA seamlessly.
→ How to set up EJBCA as a replacement for Microsoft CA
→ View overview of Microsoft Auto-enrollment and support in EJBCA
Migrate from Microsoft CA to EJBCA
Migrating your existing PKI from Microsoft's CA to EJBCA is straightforward, and opens up new possibilities for scale, performance, and throughput.
Integrate EJBCA with Azure Role Based Authentication (RBAC)
EJBCA can fully integrate with Azure's Roles, meaning that EJBCA administrators can be configured in Azure Active Directory's Groups. In doing so, EJBCA's roles no longer need to be manually populated with role members, but instead, members are automatically read from Active Directory.
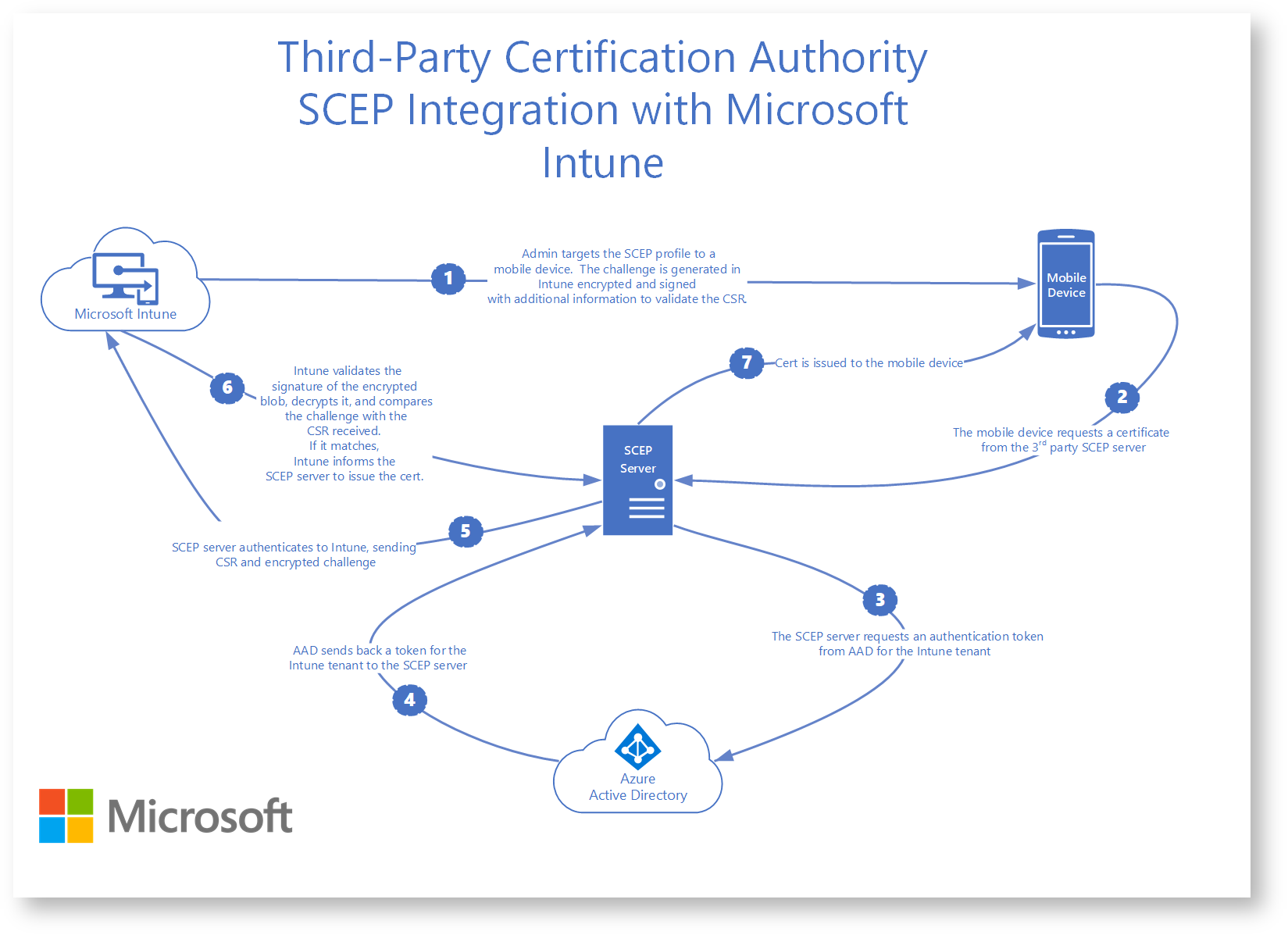
Enroll Devices over Intune
Microsoft Intune is a cloud-based service for Mobile Device Management (MDM) and Mobile Application Management (MAM), allowing the enrollment and lifecycle management of certificates to mobile devices in Microsoft Azure. Integrating Intune with EJBCA enables you to securely and remotely enroll and authenticate Microsoft Intune managed mobile devices.
Integrate EJBCA with Azure Application Insights
Application Insights is an Application Performance Management platform hosted in the Azure cloud. By integrating Application Insights and EJBCA, administrators can monitor the performance and availability of their EJBCA servers.
→ Learn more about using Azure Application Insights with EJBCA in Azure
Keep your CA Keys Secure
PrimeKey recommends using an HSM for security, compliance, and keeping all cryptographic keys secure. EJBCA supports several HSM options, including Cloud HSMs such as Azure Key Vault and Managed HSM, and Thales DPoD. For on-premises HSMs, EJBCA supports most FIPS and Common Criteria-certified HSMs, see Interoperability and Certifications.
Related Content
To learn more about how to integrate EJBCA, see EJBCA Integration and for even more guides, see Tutorials and Guides.
To find out more about other interesting solution areas and what you need to set up, see Solution Areas.