OAuth Providers
ENTERPRISE This is an EJBCA Enterprise feature.
OAuth is an open standard developed for access delegation, in which EJBCA allows a trusted third party to provide user authentication while still retaining authorization rights. OAuth authentication can be used alongside or instead of client certificate authentication (see Authentication Methods ) and provides a powerful tool for managing all users of a PKI from a single source while not needing to handle individual client credentials in the shape of client key pairs.
The following page provides an overview of OAuth providers in EJBCA. For instructions on setting up OAuth providers, see OAuth Provider Management.
Supported Providers
As of EJBCA 7.5.0, two providers have been tested with EJBCA:
For instructions on how to set up the providers, see OAuth Provider Management.
Other providers conforming to OAuth 2.0 and OpenID Connect (OIDC) may work with EJBCA, but these have not yet been tested and evaluated by PrimeKey.
Provider Configuration Overview
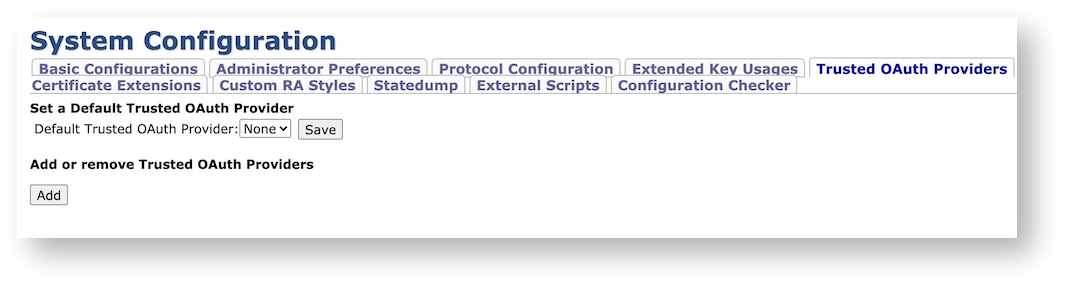
The OAuth configuration page is found under the Trusted OAuth Providers tab in System Configuration.
|
Value |
Description |
|
Default Trusted OAuth Provider |
If the received token does not have a Key ID, the Default Trusted OAuth Provider may be used to verify the signature. If authorization succeeds the token is accepted, otherwise, authorization fails. |
Generic Values
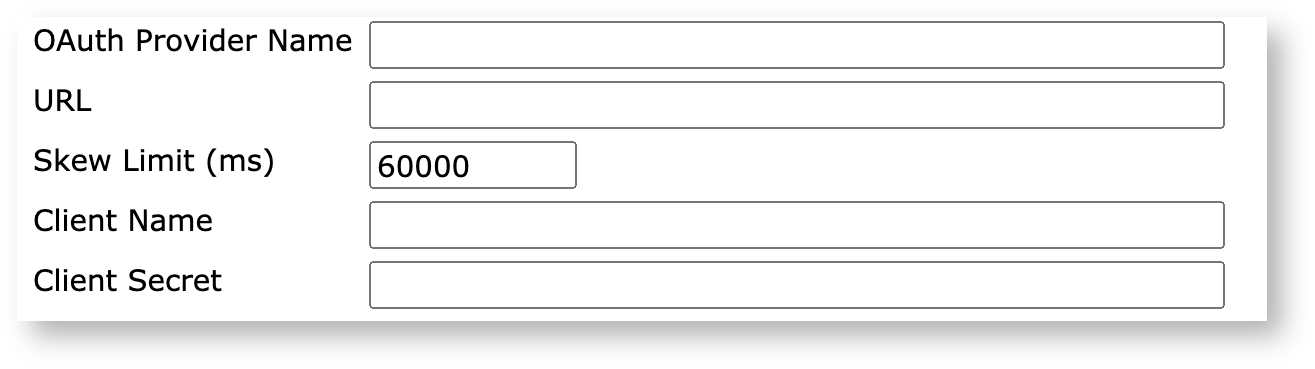
When adding an OAuth Provider, the following values exist as general options:
|
Value |
Description |
|
OAuth Provider Type |
The OAuth implementation, some of which may have distinct configuration values. |
|
OAuth Provider Name |
A human readable name for this OAuth provider. |
|
URL |
The base login URL of the provider. |
|
Skew Limit |
The allowed clock difference, in milliseconds, between the OAuth provider and EJBCA. |
|
Client Name |
The client name EJBCA uses to access the OAuth provider. |
|
Client Secret |
The client password EJBCA uses to access the OAuth provider, if required. |
At the bottom of the page is a form for providing the OAuth public key:
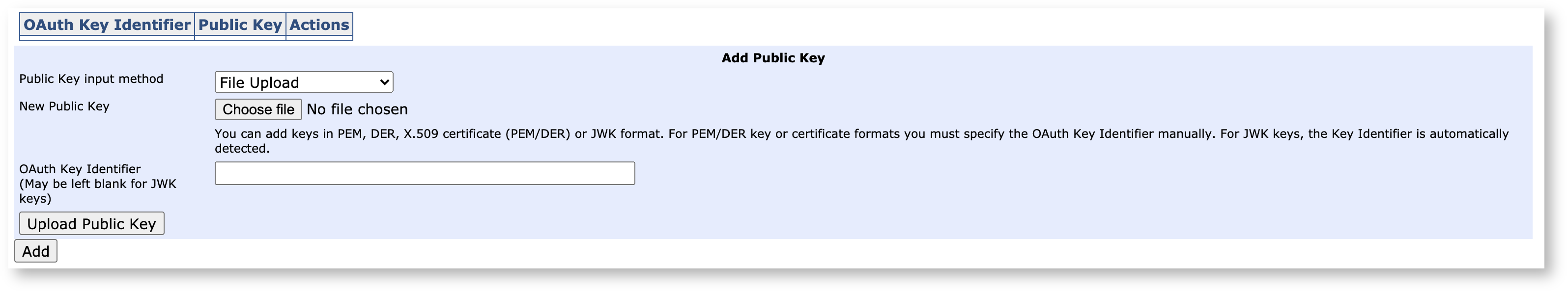
The key may be provided using three methods:
File Upload
Upload as text
Providing a Key Configuration URL
Implementation Specific Values
Besides the generic values, each supported OAuth implementation may support additional vendor specific configuration values:
Keycloak

|
Value |
Description |
|
Realm Name |
The desired Keycloak realm. |
Microsoft Azure

|
Value |
Description |
|
Tenant |
The specified tenant for this provider. |
|
Scope |
Set the scope. In the Azure Active Directory, this is configured in Expose an API → Add a scope. |
Role Member Configuration Overview
Claims in OAuth tokens may be mapped to roles. A claim can represent a group of users or an individual user. EJBCA allows any combination of claims and even different authentication methods in a single role.
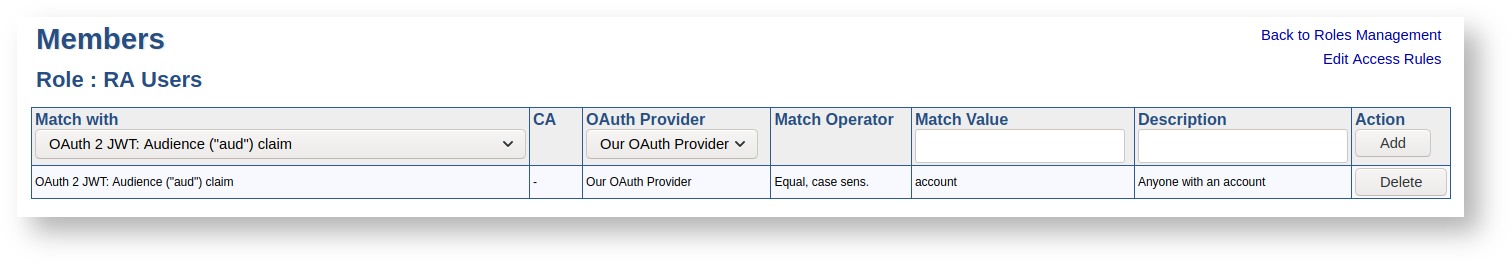
The following claims are supported. Exact usage depends on the provider, refer to the providers' documentation.
|
Claim |
Description |
|
sub |
Permanent unique identifier of the subject. When using KeyCloak, this identifies a specific user. |
|
iss |
Issuer of the token. |
|
aud |
Audience. |
|
oid |
Azure specific claim that represents a user. |