EJBCA 7.6.0 Release Notes
JUNE 2021
The PrimeKey EJBCA team is pleased to announce the release of EJBCA 7.6.0.
This release continues this spring's push to develop EJBCA as the preeminent solution for Enterprise PKIs, with further integration with Microsoft PKIs. It also brings to light External Account Bindings, an important concept for anybody needing to handle large volumes of device certificates. Included in this release are also the changes made in EJBCA 7.5.1, which was only released internally.
Deployment options include EJBCA Hardware Appliance, EJBCA Software Appliance, and EJBCA Cloud.
Highlights
External Account Bindings
Inspired by the concept of External Account Bindings in ACME (supported since EJBCA 7.5), we've extended the concept globally across EJBCA to provide a quick and easy way to link any certificate enrolled via the RA, REST, or ACME with an external identifier, to affiliate certificates to identities.
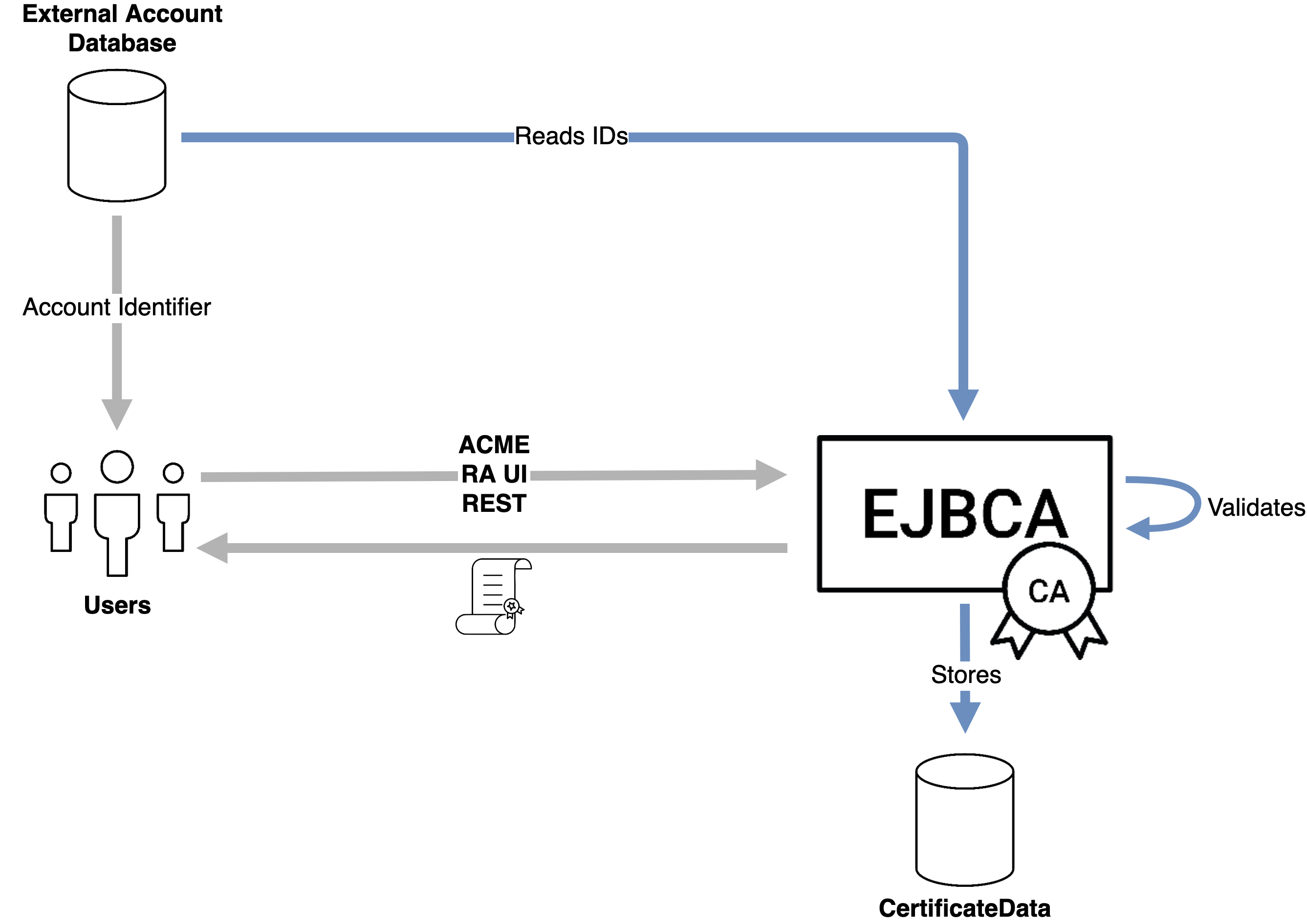
Subsets of allowed values can be pre-configured in the certificate profiles to ensure that only valid identities can be submitted, as well as providing content assistance in the RA.
Microsoft Intune Revocation and Other Improvements
Published and documented as recently as May of this year, Microsoft Intune now provides the ability to request revocation of certificates from Azure. EJBCA 7.6.0 has full support for this API in the form of a Service Worker which will periodically poll Azure for new revocation requests.
In addition, the following improvements have been made to our Intune support:
AD Authentication to Azure can now be made with a certificate instead of a username/password.
The connection between the CA and Azure can now be piped through an EJBCA RA, doing away with any requirements on the CA to have a direct connection to Azure.
Microsoft Azure Managed HSM (MHSM)
In addition to supporting Azure Key Vault, EJBCA now supports the new Managed HSM (MHSM) which offers FIPS 140-2 Level 3 for a higher assurance level to protect your keys in the cloud. Using the same REST API as Key Vault, you can add an MSHM instance as an Azure Key Vault Crypto Token (or several instances as separate crypto tokens).
Testing Baseline raised to JDK11
While JDK11 has been in use for some years among customers, we have internally raised the baseline from JDK8 to JDK11, which is now the recommended JDK to use with EJBCA. We will in the coming months be announcing the sunset of JDK8 support, and are looking forward to supporting JDK17 as soon as it's been released by Oracle.
Compliance
Compliance with CA/Browser Forum Ballot SC44
CA/Browser Forum ballot SC44 redefined some return codes for ACME, to which EJBCA 7.6.0 is now fully compliant.
Security
EJBCA 7.6.0 comes with fixes for a few minor security issues, as well as additional security hardening.
General Purpose Custom Publisher able to Run Despite External Scripts Being Disabled
It was found during testing that the General Purpose Custom Publisher, which is normally run to invoke a local script upon a publishing operation, was still able to run if the System Configuration setting Enable External Script Access was disabled. With this setting disabled it's not possible to create new such publishers, but existing publishers would continue to run. Two weeks after the release of EJBCA 7.6.0 this issue will be reported as a CVE.
Severity
Low – creating and changing a publisher would still require super admin access to EJBCA, and modifying any existing scripts would require operating system access.
Enrollment Secrets Logged in Audit Log
When audit logging changes to the alias configurations of various protocols that use an enrollment secret, any modifications to the secret were logged in cleartext in the audit log. Two weeks after the release of EJBCA 7.6.0 this issue will be reported as a CVE.
Severity
Low – enrollment secrets are already by definition known among system administrators and only trusted users should have audit log access.
Enrollment Secrets Reflected in UI
As part of the configuration of the aliases for SCEP, CMP, EST, and Auto-enrollment, the enrollment secret was reflected on the page. While hidden from direct view, checking the page source would reveal the secret. Two weeks after the release of EJBCA 7.6.0 this issue will be reported as a CVE.
Severity
Low – anybody with access to the configuration page likely has access to the secret as well, and is authorized to change the secret.
CMP Revocation Ignores Multi Tenancy Constraints
CMP RA Mode can be configured to use a known client certificate to authenticate enrolling clients. The same RA client certificate is used for revocation requests as well. While enrollment enforces multi tenancy constraints (by verifying that the client certificate has access to the CA and Profiles being enrolled against), this check was not performed when authenticating revocation operations, allowing a known tenant to revoke a certificate belonging to another tenant.
Severity
Medium – while not as serious as ignoring multi tenancy constraints for enrollment, this allowed tenants to perform DoS attacks on each other. The attacking party still needed to be a known and trusted entity.
Upgrade Information
Review the EJBCA 7.6.0 Upgrade Notes for important information about this release. For upgrade instructions and information on upgrade paths, see Upgrading EJBCA.
EJBCA 7.6.0 is included in EJBCA Hardware Appliance 3.8.0 and EJBCA Cloud 2.7.0 and can be deployed as EJBCA Software Appliance.
Change Log: Resolved Issues
For full details of fixed bugs and implemented features in EJBCA 7.6.0, refer to our JIRA Issue Tracker.
Issues Resolved in 7.6.0
Released June 2021
New Features
ECA-8220 - CMP: possibility to configure Issuing CA certificate included or not in the caPubs field
ECA-9476 - Make it possible to restore end entity and certificate data from the WildFly log file
ECA-10043 - Update Intune dependencies
ECA-10078 - Add validation and display useful error messages
ECA-10090 - Validation of uploaded EAB config
ECA-10114 - Update documentation with RA web changes
ECA-10123 - Secret Input For Custom Worker UI
Improvements
ECA-7640 - End entity editor in the RA Web
ECA-8473 - Support other authentication than password for Azure Key Vault Crypto Token
ECA-9276 - Support client certificate authentication for Azure Intune for SCEP enrollment
ECA-9553 - ACME EAB Documentation
ECA-9685 - Improve German translation for AdminWeb and RA
ECA-9832 - Security hardening
ECA-9836 - Add option to SCEP Alias to disable SHA-1 digest algorithm in responses
ECA-9936 - Add handling of unsupported role member types
ECA-9942 - Compile statedump-ejb without access to appserver
ECA-9996 - Migrate the OCSP transaction log and the OCSP audit log to the GUI
ECA-10001 - Give ACME aliases with EAB the option to generate the symmetric key
ECA-10021 - Add EAB support to REST for /v1/certificate/pkcs10enroll
ECA-10028 - Update REST Search functionality with the EAB ID
ECA-10029 - Add the EAB ID field to the RA Enroll page
ECA-10034 - Decide in a format that has namespace support
ECA-10061 - Security hardening
ECA-10064 - Language improvement and typo updates
ECA-10065 - Support Azure MHSM as a Key Vault crypto token
ECA-10079 - Help text on EAB upload page
ECA-10098 - Preview of uploaded EAB namespaces under System Configuration
ECA-10101 - Security hardening
ECA-10102 - Multi-select for EAB Namespaces in Certificate Profile
ECA-10165 - IntuneRevocationWorker is missing setting for AUTH_AUTHORITY
Bug Fixes
ECA-7972 - CN is not copied to dNSName when "Use entity CN field" is enabled in the end entity profile
ECA-9330 - Security Issue
ECA-9558 - Multiple choices of the same curves in certificate profile - unable to enroll ECDSA prime256v1 certificate via RA Web
ECA-9660 - Cannot enroll over ACME using an EC keypair
ECA-9975 - Pre-produced OCSP responses are only published to the first VA
ECA-9985 - DeltaCRL creation time
ECA-9999 - Incorrect response to ACME challenge URL when using POST-as-GET
ECA-10020 - Regression: CSR Upload in the RA Web causes spontaneous redirect to blank page
ECA-10022 - Fix ACME pre-authorization NPE and empty list of authorizations
ECA-10044 - Fix ACME EAB shared key encryption from RA
ECA-10048 - Security issue
ECA-10073 - Saving CA resets Subject Alternative Name field
ECA-10082 - Security issue
ECA-10083 - Autoenrollment: Clear header from outgoing SOAP message when one already exists
ECA-10088 - Autoenrollment: Enrollment permission check is too strict
ECA-10089 - Security issue
ECA-10093 - SSH settings must not be displayed in CE edition End-Entity Profile edit form
ECA-10097 - Regression: Security exception and missing classes on classpath when importing using EJBCA DB CLI
ECA-10104 - Regression: Exception occurs when viewing certificate
ECA-10106 - Signing of data larger than 20 KiB with ECDSA and PKCS#11 NG (e.g. eIDAS HSM) fails
ECA-10109 - Signing of data larger than 20 KiB with AWS KMS and Azure Key Vault fails
ECA-10113 - Maximum number of failed login attempts not working via RA Web
ECA-10116 - Run CRL partition index db update in post-upgrade instead of upgrade at a startup
ECA-10122 - Unable to set Intune key binding in SCEP configuration
ECA-10125 - Intune Scep Serialization Error
ECA-10129 - Intune revocation missing SCEP fields
ECA-10132 - Azure Crypto Token using cert auth with auto activation shows inactive when restarting wildfly
ECA-10133 - Fix selenium
ECA-10134 - EAB namespaces broken for configdump
Issues Resolved in 7.5.1
Internally Released May 2021
New Features
ECA-9270 - Allow Intune verification to be performed from the RA
ECA-9441 - Implement support for a keystore using FIPS compliant algorithms
ECA-9972 - Create a Service Worker for Intune Revocation
ECA-10010 - Use configured CAs
ECA-10016 - SCEP servlet should update intune after cert issuance
Improvements
ECA-9658 - ACME agree to new ToS
ECA-9792 - Add a button for importing certificates to an OCSP responder
ECA-9833 - Configdump SCEP Import/Export with Intune settings
ECA-9898 - ACME: Limit followed redirect codes according to CABForum Ballot SC44
ECA-9974 - The domain ignore list used for CAA validation should be consistent with how domains names in certificates work
Bug Fixes
ECA-9372 - "Any CA" in Ocsp Pre-Signer Service has no effect
ECA-9408 - Security hardening
ECA-9903 - Remove Apache Velocity from /lib
ECA-9977 - Regression: ejbca.sh fails to import endentities profiles with notifications - need commons-lang3
ECA-9984 - Allowed Characters changing after disabling User Storage
ECA-10000 - p11ng-cli signperformancetest calculates signings per seconds incorrectly
ECA-10007 - MSAE Configuration displays in VA instances
ECA-10017 - Fix FindBugs warnings related to OAuth