Configure EJBCA for Public Access
The following covers how to enable public access to the EJBCA RA UI and to the EJBCA CA UI.
Enabling Public Access to the EJBCA RA UI
An RA or CA can be configured for public access using a PublicAccessAuthenticationToken. Public access allows anyone to navigate to the RA UI without having to present a client certificate (this would normally be port 8442 instead of 8443 if you have set up EJBCA with 3-port separation, see Use 3-Port Separation application server configuration instructions).
You can configure EJBCA for public access either using the CA UI or the EJBCA CLI.
Configure Public Access using the CA UI
To configure EJBCA public access, go to System Functions → Roles and Access Rules and add a new member to any role. The member should have Match with set to one of the following:
PublicAccessAuthenticationToken : Any transport (HTTP or HTTPS)
PublicAccessAuthenticationToken: Non-confidential transport (HTTP)
PublicAccessAuthenticationToken: Confidential transport (HTTPS)
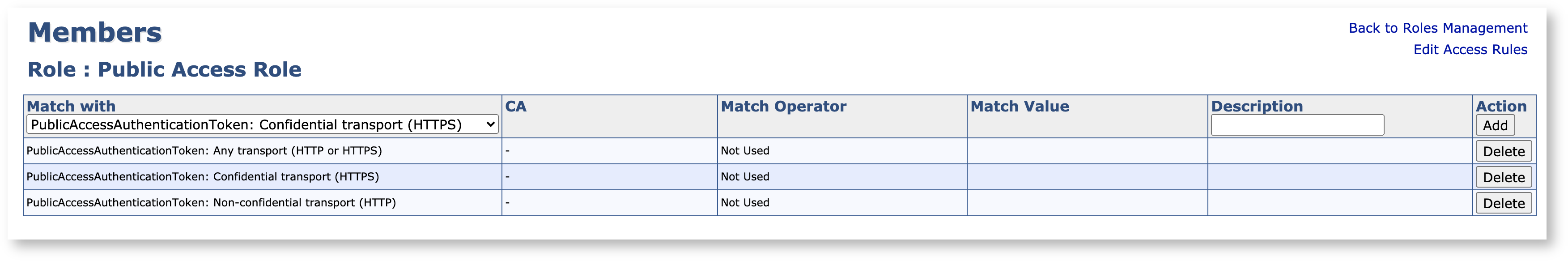
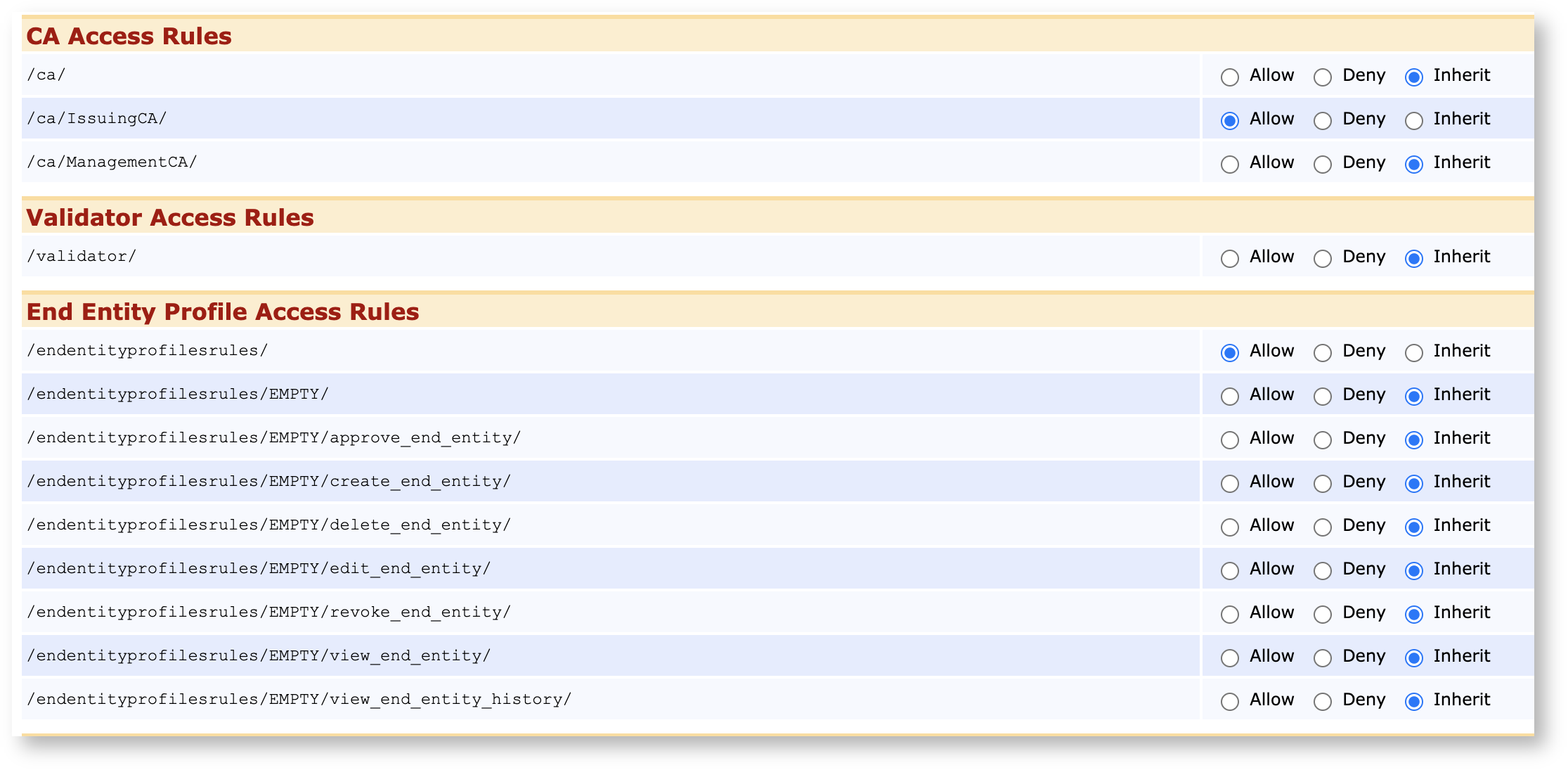
Next, click Access Rules for that role, go to Advanced Mode and give this role the following access rights:
Access to /ca_functionality/create_certificate/:

Access to the CAs and End Entity Profiles that you wish to be publicly accessible. For more details, see RA Administrator Access Rules.
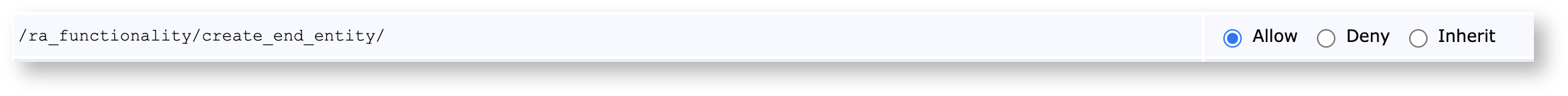
Optionally, to let the public user create new end entities and have access to the Make New Request page, they need to be given the access rule /ra_functionality/create_end_entity/:
Optionally, let the public user enroll with existing end entities, via the "Use Username" or "Use Request ID" pages:

Optionally, to let the public user access to CA Certificates and CRLs page, they need to be given the access rule /ca_functionality/view_ca:

This will produce a minimal enrollment interface for anybody to use.
Note that public users cannot use the EMPTY End Entity Profile when choosing Key-pair generation "By the CA" since that would require the public role to have ROOT access to EJBCA.
Configure Public Access using the EJBCA CLI
To configure EJBCA for public access using the CLI, run the following:
./ejbca.sh roles addrolemember --caname "" --role "Super Administrator Role" --value "" --with PublicAccessAuthenticationToken:TRANSPORT_ANYThis will disable client certificate authentication in EJBCA for the RA. Alternatively, instead of allowing both HTTP and HTTPS using TRANSPORT_ANY it is possible to allow only HTTP using TRANSPORT_PLAIN and only HTTPS using TRANSPORT_CONFIDENTIAL.
Enabling Public Access to the EJBCA CA UI
Please note that this operation would make the CA UI publicly available to any party and would in almost all cases cause a gaping security risk. Make sure you know what you're doing before you disabling the web.reqcert property.
To disable all authentication checking to the CA UI, recompile setting web.reqcert=false in conf/web.properties.