EJBCA 7.8.1 Release Notes
DECEMBER 2021
The PrimeKey EJBCA team is pleased to announce the release of EJBCA 7.8.1.
This release has seen a primary focus on improving our REST API, as well as further integration with the Microsoft ecosystem.
Deployment options include EJBCA Hardware Appliance, EJBCA Software Appliance, and EJBCA Cloud.
Highlights
REST API Improvements
ConfigDump over REST
Our ConfigDump tool, used to manage and audit EJBCA configurations through human-readable YAML, can now be accessed over REST, both for export and import. This allows easy use of the ConfigDump tool for the Hardware and Software Appliances, Cloud and other platforms without command-line interface access.
New REST calls and improvements
End Entity Search extended with MODIFIED_DATE.
Added pagination to certificate search endpoint.
Added a new certificate enrollment endpoint that prioritizes predefined end entity values over values defined in the CSR.
Added End Entity Profile and Certificate Profile names to the search results of certificate searches.
For more information, see EJBCA REST Interface.
Microsoft Integration
EJBCA Roles can be populated through Azure Active Directory
EJBCA's roles can now have its members populated by corresponding Active Directory Groups through Azure Role Based Authentication (RBAC). What this means is that when using Azure as an OAuth provider for authenticating to EJBCA, role members don't need to be manually populated but can instead be automatically read from existing AD Groups. For more information, see Integrating EJBCA with Azure AD Role Based Authentication (RBAC).
Integration with Microsoft Application Insights
Application Insights is an Application Performance Management (APM) service hosted in the Azure cloud platform that allows DevOps professionals to monitor live applications. By integrating Application Insights and EJBCA, administrators can monitor the performance and availability of their EJBCA servers. For more information, see Integrating EJBCA with Azure Application Insights.
Domain Allow List Validator
By popular request, we've added a companion Domain Allow List Validator to the existing Domain Block List Validator. Performing the exact opposite role, this new validator restricts dnsName field domains to whatever subset is defined. For more information, see Certificate Field Validators.
URIs Added as Name Constraints
In addition to constraints on DNS Name and IP Address, we've added name constraints for URIs. For more information on name constraints, see CA Fields.
Sunset of ejbca-setup.sh Script
We are sunsetting the ejbca-setup.sh quick installation script and associated documentation to decrease the maintenance load and consolidate the installation paths. If you're currently relying on this script, we recommend you migrate your workflows.
Basic HTTP Authentication for EST
When using EST in client mode, it's now possible to authenticate over HTTP with username/password.
Bouncy Castle Upgraded to Version 1.70
Just in time to make this release, we upgraded Bouncy Castle to the latest version.
Support for Oracle19C
We have implemented support for the Oracle 19C database
Compliance
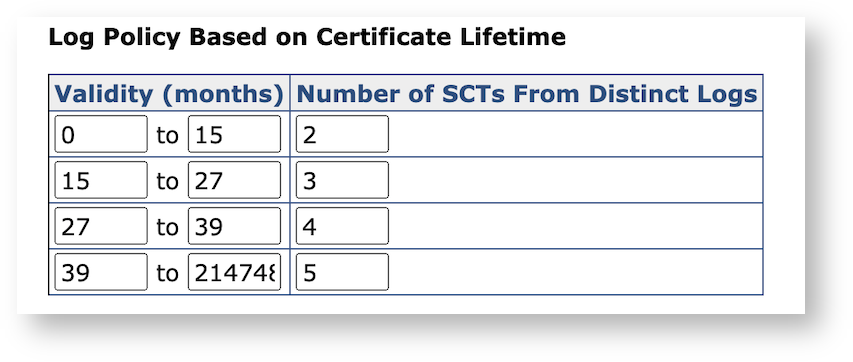
Added Granularity to Certificate Transparency Configuration
Due to CT Policy Updates in Apple's Root Program, the configuration of the number of required Signed Certificate Timestamps (SCTs) per time interval has been made fully granular.
Possible to add empty dnsName values and URIs as Name Constraints
As per name constraints discussions in the CA/Browser Forum Validation Working Group, we've added the ability to add an empty DNS name to name constraints. Adding this value constrains a Sub CA from issuing any certificates containing dnsName SAN values. For more information on name constraints, see CA Fields. We've also taken the chance to add URIs as possible Name Constraint values.
Upgrade Information
Review the EJBCA 7.8.1 Upgrade Notes for important information about this release. For upgrade instructions and information on upgrade paths, see Upgrading EJBCA.
EJBCA 7.8.1 is included in EJBCA Hardware Appliance 3.9.3 and EJBCA Cloud 2.9.2 and can be deployed as EJBCA Software Appliance.
Change Log: Resolved Issues
For full details of fixed bugs and implemented features in EJBCA 7.8.1, refer to our JIRA Issue Tracker.
Issues Resolved in 7.8.1
Released December 2021
New Features
ECA-9561 - ACME IP Identifier Validation http-01 Challenge
ECA-9760 - REST searchCertificates call with pagination
ECA-10108 - Merge additional support for the NONEwithRSAandMGF1 (raw RSASSA-PSS) signature algorithm in P11NG
ECA-10184 - KeyVault Machine Identity Authentication
ECA-10334 - HTTP Basic Authentication in EST client mode
ECA-10344 - REST API support for configdump export
ECA-10347 - REST API support for configdump import
ECA-10349 - Add configdump support to Azure BLOB publisher
ECA-10356 - Add Primus HSM PKCS#11 library path
ECA-10380 - Domain Allow List Validator
ECA-10395 - Add support for URI Name Constraints
Improvements
ECA-5472 - Foldable view when there are many optional fields in the RA
ECA-8562 - Improve tests coverage of Configdump's import of Certificate Profiles
ECA-8745 - Increase the number of SANs configurable in end entity profiles (to >100)
ECA-9681 - Fix AcmeOrderData end entity stored including binary data as map
ECA-9763 - Change the message for CA Activation with approvals
ECA-10092 - Add cert auth to Azure Trusted OAuth Provider
ECA-10266 - Upgrade Nimbus JOSE+JWT to nimbus-jose-jwt-9.12.1.jar
ECA-10284 - Check if all invocations of AcmeAccountSessionBean.updateAccount are required
ECA-10293 - Bad signature performance using P11-NG with network HSMs
ECA-10302 - Revoking certificates from adminweb with reason 'Privileges withdrawn'
ECA-10318 - Add roles claim to Azure OAuth for Authentication
ECA-10322 - Create tables SQL script for NDB cluster has flaws
ECA-10324 - Combine ACME and general EAB
ECA-10327 - Reduce CRL and OCSP Validities by 1 second
ECA-10330 - Change default settings SCT in EJBCA 7.x
ECA-10333 - REST Search - Return eep and cp values
ECA-10339 - Viewing CRL's for CA with MS Compat Enabled
ECA-10345 - Put PIN last in the GUI when creating crypto token
ECA-10352 - MS CA compat with Sub CA in EJBCA and External Root
ECA-10353 - Allow name constraints to block all DNS Names
ECA-10354 - Fix ACME pre-authorization returns order object without authorization
ECA-10355 - Update EJBCA to work with Wildfly 25
ECA-10358 - ACME performance - refactor AcmeOrderSessionBean.processPendingOrders
ECA-10360 - Add aliases cache for P11-NG crypto tokens
ECA-10361 - PKCS#10 REST endpoint using end entity information (not CSR)
ECA-10367 - Optimize PKCS#11 sign to avoid redundant PKCS#11 calls
ECA-10377 - EE REST API support search by modified date
ECA-10382 - Allow to configure ignored CAA properties when their processing is done outside EJBCA
ECA-10384 - Differentiate rows in CA Structures & CRLs
ECA-10398 - Align buttons in Certificate Profile and Publishers sections
ECA-10400 - X509CACrlUnitTest test fix
ECA-10406 - Merge smaller P11-NG changes from SignServer
ECA-10428 - Remove extra dot from cert
ECA-10430 - Upgrade BC to 1.70
Bug Fixes
ECA-6166 - CA key export does not warn if no RSA keys are present for encryption.
ECA-7235 - Settings are reset when Match with setting is changed
ECA-8227 - It is possible to revoke an already revoked end entity
ECA-9203 - Exception occurrs even if 'Gender' value is given
ECA-10126 - Error when syncing to VA via peer connector
ECA-10157 - Security Issue
ECA-10172 - EST Vendor Mode ChangeSubjectName should not compare with the CSR DN
ECA-10224 - CREATE CA: NullPointerException
ECA-10229 - CMP Authentication Radio Buttons are not disabled in view page
ECA-10237 - Trusted OAuth Providers are removed without any warning or confirmation
ECA-10254 - SCEP alias for Intune not allowing certain characters for client secret.
ECA-10264 - Configdump import failed if the /cryptotoken/keys/remove/ rule is set
ECA-10295 - Configdump does not import Approval Profiles
ECA-10301 - Revoking certificates from adminweb with reason 'AA compromise'
ECA-10303 - Throwaway CA Revocation Broken in 7.6.0
ECA-10311 - View CMP Alias page says: Edit CMP Alias
ECA-10319 - Broken RA End Entity edit page
ECA-10320 - OCSP not working when CA uses Ed25519
ECA-10323 - Enrollment code can not be empty when setting EE status from Generated to New with autogenerated enrollment codes
ECA-10343 - NumberFormatException when creating a crypto token using token label when cryptotoken.p11.lib.X.slotlist is used
ECA-10357 - Ignore keys which cannot be read by the P11NgCryptoToken
ECA-10363 - Make audience check optional
ECA-10365 - Fix links in ACME HTTP response headers
ECA-10383 - In RAWeb custom values "Set validity" doesn't work
ECA-10390 - "Republish" publisher queue view action uses wrong PublishQueueProcessWorker
ECA-10391 - 'Required' restriction on name constraints in end entity profiles are not validated.
ECA-10394 - Clean up of cesecore-p11 is not optional
ECA-10399 - ExpiredCertsOnCRL encodes with fractional seconds
ECA-10404 - Make EEP upgrade for 7.8.1 cluster compatible
ECA-10407 - Audience cannot be empty when "disable audience check" is selected
ECA-10410 - Reintroduce ECA-9475
ECA-10422 - Fix failing tests