EJBCA 7.5 Release Notes
MAY 2021
The PrimeKey EJBCA team is pleased to announce the release of EJBCA 7.5.0.1. ( EJBCA 7.5.0 was an internal release, not generally available for customers.)
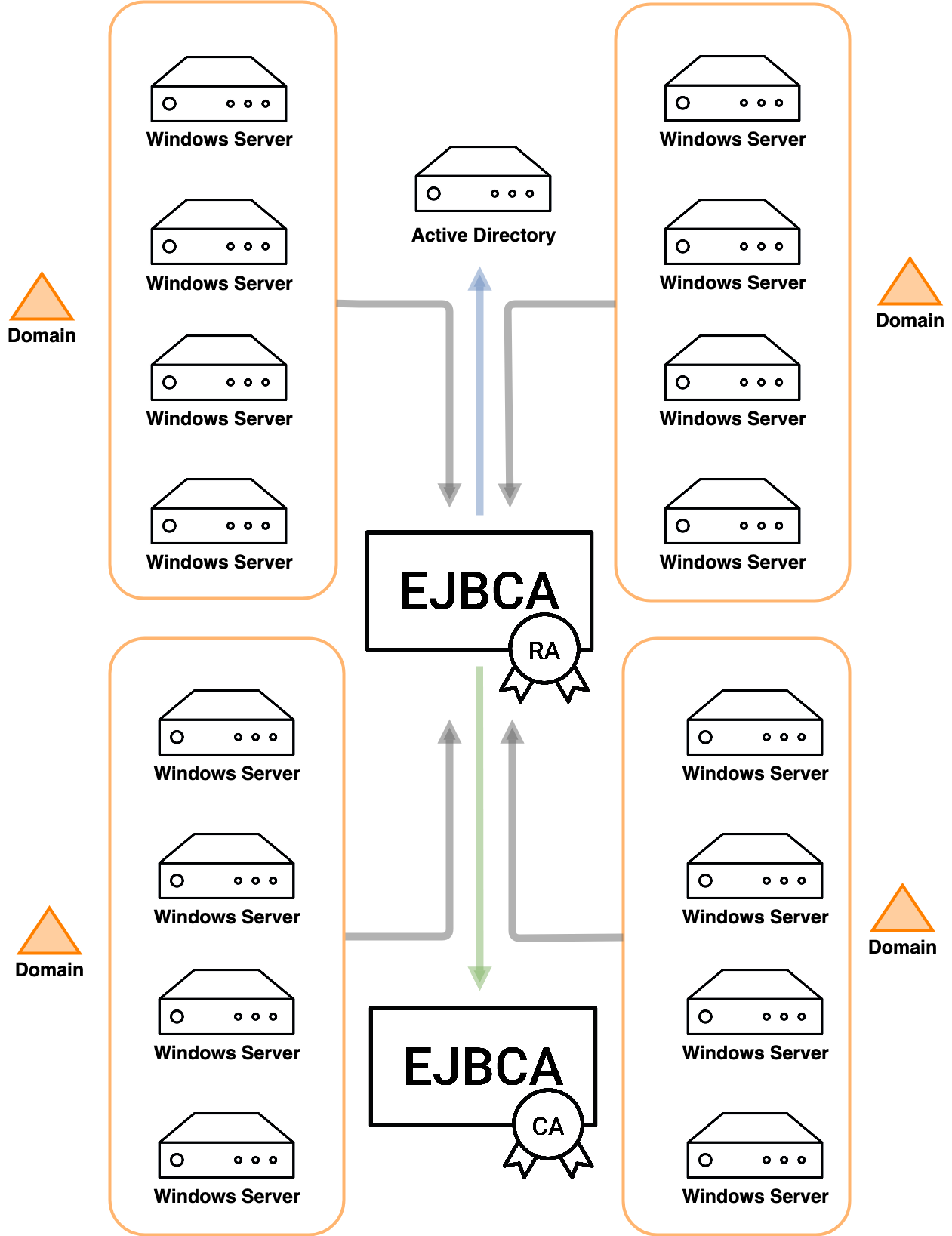
The primary focus of this release has been integration with other elements of the PKI ecosystem, not least of which full integration of Microsoft Auto-enrollment into the EJBCA RA and support for authenticating to the CA and RA UIs and REST through OAuth.
Deployment options include EJBCA Hardware Appliance, EJBCA Software Appliance, and EJBCA Cloud.
Highlights
Microsoft Auto-enrollment Integration
Until now PrimeKey has supplied an Auto-enrollment proxy in order to allow customers to integrate single domain Microsoft PKIs with EJBCA as a backend.
From version 7.5, EJBCA now has Microsoft Auto-enrollment support fully integrated, not only transcending the need for a proxy but also eliminating the need for a Certificate Enrollment Policy server or Certificate Enrollment Server, with the EJBCA RA being the point of first contact for enrolling clients. EJBCA 7.5 also allows for multi forest support, letting all your domains integrate into a single PKI through the same endpoint. For more information, see Microsoft Auto-enrollment Overview.
With the new Microsoft Auto-enrollment integration in EJBCA 7.5, we are announcing end of sale and end of support for the former PrimeKey Auto-enrollment proxy.
End of sale as of EJBCA Enterprise 7.5.
End of support and maintenance in May 2022.
OAuth Authentication to the EJBCA CA and RA UIs and REST API
Moving on from the classic support for client certificates to access the CA and RA UIs, and the REST API, EJBCA 7.5 now supports access using an OAuth provider over OpenID. So far we've tested and confirmed authentication using KeyCloak and Azure Active Directory.
ACME External Account Bindings
Long requested, we've implemented ACME External Account Bindings in accordance with RFC 8555 section 7.3.4. External Account Bindings allows the client to specify a unique ID number that is associated with that ACME account, and in our implementation we've associated the ID with each issued certificate for easy lookup later. In addition to being able to authenticate the ID using a MAC as per the RFC, we've also allowed for using a signature from a locally issued certificate instead.
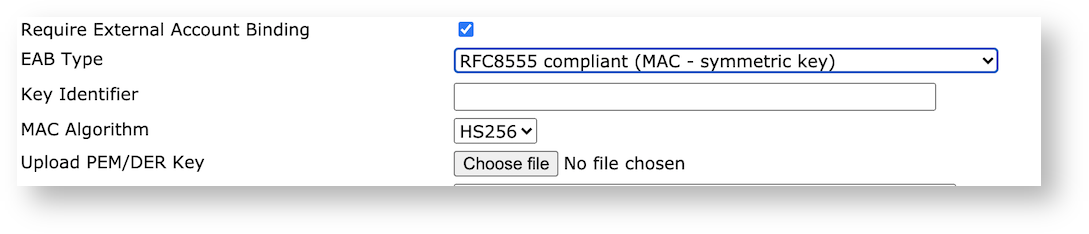
For more information on managing ACME External Account Bindings in EJBCA, see ACME.
EST Client Mode
We've added Client Mode to EST as with CMP and SCEP. Unlike RA mode, Client Mode only allows issuance against previously created end entities and does not automatically enroll new ones. This workflow is optimal for IOT use cases, where a limited set of devices need to enroll to your PKI.
HSM support for Ed25519 and support for AWS Cloud HSM
Apart from earlier software support for the signature algorithms Ed25519 and Ed448, support has been added for using Ed25519 with selected HSMs which support Ed25519, starting with nCipher nShield, Thales Luna and SoftHSMv2. This support is only available when using P11-NG Crypto Tokens in EJBCA. In conjunction with this, EJBCA is now fully compatible with the AWS Cloud HSM.
Compliance
OCSP Support Updated to Conform to RFC 8954
We have updated our OCSP responder to conform with the clarifications specified in RFC 8954, specifically to how EJBCA handles client generated nonces.
eIDAS Compliance
Support has been added in the CA UI for easy editing of the new Legislation Country QC Statement as specified in ETSI EN 319 412-5 v2.3.1 section 4.2.4.
Support for multiple SemanticIdentifier to a single certificate, i.e. to specify both EN 319 412-1 Natural Person and Legal Person at the same time.
CAs can now be configured to automatically generate a CRL upon revocation.
CA/Browser-Forum Compliance
Ballot SC44 limits the allowed redirect codes by complying CAs. These changes are planned to be implemented in EJBCA in version 7.6, due in the end of May.
Upgrade Information
Review the EJBCA 7.5 Upgrade Notes for important information about this release. For upgrade instructions and information on upgrade paths, see Upgrading EJBCA.
EJBCA 7.5.0.1 is available on
EJBCA Hardware Appliance 3.7.1
and
EJBCA Cloud 2.6.1 and can be deployed as EJBCA Software Appliance.
Change Log: Resolved Issues
For full details of fixed bugs and implemented features in EJBCA 7.5, refer to our JIRA Issue Tracker.
Issues Resolved in 7.5.0.1
Released May 2021
New Features
ECA-6630 - Create YAML export for CMP configuration
ECA-6689 - Not possible to issue CA certificates through the RA web
ECA-9441 - Implement support for a keystore using FIPS compliant algorithms
ECA-9484 - Support for Ed25519 in P11NG
ECA-9490 - General Account Binding (GAB)
ECA-9491 - ACME External Account Binding (EAB)
ECA-9492 - ACME EAB Configuration UI
ECA-9494 - ACME EAB Implementation as specified in RFC8555
ECA-9495 - ACME EAB Implementation for public key signature validation
ECA-9500 - Add support for new eIDAS QC statement esi4-qcStatement-7, Legislation
ECA-9525 - Optionally, add cache header for OCSP unauthorized response
ECA-9527 - Add Role as standard DN field
ECA-9550 - Prevent deployment of EJBCA after a hardcoded date
ECA-9561 - ACME IP Identifier Validation http-01 Challenge
ECA-9572 - Create MSAE Servlet module in EJBCA
ECA-9633 - Support Thales DPoD
ECA-9671 - Option to disable http-01 challenge for ACME wildcard certificates
ECA-9696 - Make the ACME order validity configurable
ECA-9724 - Add XCEP implentation in the msae package
ECA-9737 - Add EST client mode
ECA-9738 - CLI support to create new Crypto Token with Azure key vault (ejbca.sh ca cryptotoken)
ECA-9762 - Read token and give access (RA Web)
ECA-9767 - Add MS Intune Azure Active Directory authentication URL to SCEP alias
ECA-9771 - Add Intune verification Auth. URL to SCEP alias configuration
ECA-9780 - Add MSAE to protcol configuration
ECA-9816 - Add Intune resource URL and Graph related fields to SCEP alias configuration and mask app key field
ECA-9817 - Add CRL generation upon revocation and configdump
Epics
ECA-9005 - Integrate Microsoft Autoenrollment (MSAE) into the EJBCA RA
ECA-9624 - OAuth Support
ECA-9716 - CRL Generation upon revocation
Improvements
ECA-4750 - Change default configuration of User Notice text to use UTF-8
ECA-7391 - Only show CA-related approvals in CA Web (and vice versa)
ECA-7844 - The space before the Validator name is not trimmed
ECA-8350 - Implement 'revokeCert' resource authorization for an ACME account holding all of the identifiers in the certificate
ECA-8705 - Deleting items with dependencies
ECA-8940 - Make P11-NG an optional provider for EJBCA
ECA-9006 - Certificate Template Enrollment Authorization Bypass
ECA-9282 - Replace outmoded language in EJBCA
ECA-9361 - Add "Flush" and "Republish" to publisher queue view
ECA-9378 - Improve the error logging for OCSP response generation
ECA-9475 - Make REST search result limit rely on global config
ECA-9489 - Add support for key unwrapping in P11-NG provider
ECA-9526 - Fix OWASP job in Jenkins
ECA-9532 - ACME system test failures
ECA-9533 - ACME EAB config dump
ECA-9540 - Selenium setup script fails in EJBCA CE
ECA-9554 - Update nimbus-jose-jwt-8.19.jar to latest release 9.1.2
ECA-9573 - Invoke RaMasterApi from MSAE Servlet
ECA-9600 - Documentation improvement: E-mail Notification Configuration in EEP
ECA-9608 - Separate CP5 functionality from regular P11 in P11-NG
ECA-9611 - ACME EAB UI layout and code convention improvements
ECA-9612 - Log which CMP message type is received
ECA-9613 - Improve ACME EAB ConfigDump
ECA-9626 - Add selenium tests for ECA-8705
ECA-9627 - Improve ACME EAB Implementation for public key signature validation GUI
ECA-9628 - Issue a qualified certificate with multiple Semantics Identifier (OIDs)
ECA-9629 - Library upgrade in MSAE Servlet
ECA-9646 - Re-enable OAuth configuration in CA UI
ECA-9657 - Configure Keycloak login url
ECA-9664 - MSAE Servlet Kerberos authentication
ECA-9667 - Fix failing unit tests in Jenkins
ECA-9670 - Improve Documentation: Remove meaningless instruction in REST example script
ECA-9673 - Change kerberos configuration runtime
ECA-9687 - Improve clean up of ACME nonce data
ECA-9701 - Make it possible to query different AD machines from EJBCA server.
ECA-9704 - OAuth login page for RA UI
ECA-9715 - Improve caching for Azure Crypto Token
ECA-9718 - Unit test for OAuth request
ECA-9720 - Minor UX improvements for OAuth
ECA-9728 - Query AD Policies from XCEP Service
ECA-9729 - Encrypt ACME EAB symmetric key
ECA-9730 - Make the CES (MSAE) implementation a Java WebService
ECA-9731 - Option to use SSL / TLS AD connection in MSAE
ECA-9732 - UI Configuration for MSAE
ECA-9753 - Merge CertUtils and CertTools
ECA-9754 - Convert AD time format to Java
ECA-9761 - Fix JSF dynamic UI components update of value range
ECA-9766 - Replace static list of AD Templates in MSAE UI Configuration
ECA-9772 - Refactor MSAE AD Connection
ECA-9773 - CEP Service: Invoke AD connection from external package
ECA-9774 - CES Service: Invoke AD connection from external package
ECA-9775 - Create unit tests for MSAE ASN1 helper class
ECA-9784 - Add default P11 provider path for AWS CloudHSM
ECA-9785 - Rename PKCS#11 CP5 to PKCS#11 NG in crypto token driver select list
ECA-9796 - Add a CLI command to view detailed information about an OAuth provider
ECA-9804 - MSAE UI option for policy name
ECA-9811 - Support SHA256 and SHA512 RSA signatures for certificates issued by RSA based SSH CAs
ECA-9835 - Read AD templates dynamically from CESService
ECA-9838 - REST End Entity Management enabled by default
ECA-9845 - Try to authenticate using OAuth when client certificate authentication fails
ECA-9846 - Pin OAuth role members to a specific provider
ECA-9858 - Support SHA224WithECDSA in P11-NG
ECA-9875 - REST unable to pkcs10Enroll when EE profile uses auto generated password
ECA-9878 - ACME pre-authorization system test
ECA-9894 - Allow usage of JWK public key for OAuth
ECA-9901 - Strip trailing slash from OAuth URL for KeyCloak providers
ECA-9907 - Update mapped AD template settings
ECA-9910 - Set ACME problem response content type to application/problem+json
ECA-9913 - Fallback to database is CEP Service CA cert isn't found in cache.
ECA-9917 - Prevent the user from adding public keys with duplicate keyids
ECA-9923 - Administrator name should not be UUID when logging in with KeyCloak
ECA-9960 - Revisit MSAE libs
ECA-9964 - Allow CEP service to represent multiple CAs
ECA-9965 - Rename default provider type
Bug Fixes
ECA-6010 - CLI importcacert can't import CA chain certificates
ECA-7447 - Disable "set password" in RA web if end entity profile enrollment code is "auto-generated"
ECA-7485 - EEP default CA selection doesn't work on adminweb EE creation and RaWeb enrollmakenewrequest pages
ECA-8499 - Not possible to mix Sun PKCS#11 and CP5 PKCS#11 tokens
ECA-8947 - The CLI command mergecatokens is not working for CAs with token type provider Pkcs11NgCryptoToken
ECA-9140 - CA Structure & CRLs links do not work if CA DN contains &
ECA-9155 - Certificate is generated without Username
ECA-9317 - When "Use entity CN field" In The EEP is Enabled, it is not visible on adminweb while adding EE
ECA-9499 - Security Issue
ECA-9534 - Wrong label in end entity profile: "UID, Unique Identifier" subject DN field should be "userid"
ECA-9543 - Fix DynamicUiProperty / DynamicUiModel property validation.
ECA-9544 - Insert DynamicUiModel JSF into existing table grid
ECA-9545 - Fix DynamicUiProperty / DynamicUiModel component enabling / visibility
ECA-9546 - Adding RA Proxying of EjbcaWS.softTokenRequest
ECA-9549 - Incorrect encoding of non-english languages in RA web on Java 11
ECA-9558 - Multiple choices of the same curves in certificate profile - unable to enroll ECDSA prime256v1 certificate via RA Web
ECA-9565 - Make the CE index page show the correct version information
ECA-9568 - Remove the final/static keywords from EJB methods
ECA-9586 - Regression: First letters of first DC component in CA DN always capitalized
ECA-9590 - CA signing algorithm suggestion defaults to SHA1WithRSA after selecting crypto token
ECA-9615 - Regression: When selecting multiple keys in a crypto token the wrong key(s) are removed
ECA-9619 - Remote internal key binding updater service fails with nullpointer exception
ECA-9622 - Null pointer exception is thrown when the CA tries to issue a certificate using a corrupt CSR
ECA-9630 - Regression: EST re-enroll stopped working due to authorization of re-enrolling entity
ECA-9632 - ExtendedInformation is not parsed correctly by SecureXMLDecoder for some values
ECA-9634 - Fix ACME revokeCert resource for revocations for account holders having all authorizations for the identifiers in a certificate
ECA-9638 - Fix ACME EAB exception handling
ECA-9640 - CMP 3GPP: Unable to enroll Ericsson eNodeB in Vendor Mode
ECA-9656 - EJBCA will debug log a private key if sent with CSR
ECA-9660 - Cannot enroll over ACME using an EC keypair
ECA-9661 - No check if Allow Subject DN Override by CSR in REST
ECA-9666 - Missing space in TLS error message
ECA-9675 - SCEP – null name for End Entity generated instead of DN serialNumber
ECA-9714 - Some system tests failing on processing PKCS10 requests
ECA-9721 - Error Admin UI rendering creating CAs with crypto token errors
ECA-9726 - Regression: error about ApprovalData column when exporting using ejbca-db-cli
ECA-9727 - REST API fail to enroll CSR with Subject Directory Attribute
ECA-9736 - Regression: Add/Edit End Entity actions are not logged to Audit Log
ECA-9741 - RA web ignores Subject Directory Attributes in user CSR
ECA-9749 - Regression: Intune not working, upgrade intune libraries
ECA-9764 - Fix failing configdump unit tests in Jenkins
ECA-9765 - Regression: EjbcaWS.processSoftTokenReq does not work when end entity already exist
ECA-9768 - REST API: NullPointerException enrolling end entity without ExtendedInformation
ECA-9783 - Warnings printed from CEP Service on startup
ECA-9802 - Regression: Response to acme endpoints is not correct in all cases.
ECA-9805 - Enrollment code not shown in RA web when using key recovery
ECA-9806 - AlgorithmTools is spamming the log, lower log level for list of available algorithms
ECA-9807 - Workaround C_GetAttributeValue bug in AWS CloudHSM
ECA-9808 - CE build broken. Package org.cesecore.keys.token.p11ng.provider does not exist (in CE)
ECA-9809 - Unable to sign RSA public keys with SSH CA
ECA-9815 - OAuth login page is not shown when authentication fails on a JSP page
ECA-9822 - Regression: ejbcaClientToolBox.bat does not work
ECA-9824 - Edit CA resets Extended Services Key Specification for CMS CA Service
ECA-9839 - Theoretical NPE in EjbcaWebBeanImpl
ECA-9841 - OAuth provider without keys cannot be deleted
ECA-9847 - Regression: Missing library in CMP HTTP proxy
ECA-9851 - OAuth Client Secret should be input type password
ECA-9853 - OAuth refresh token assumes there is also an access token
ECA-9855 - Security issue
ECA-9859 - Read profiles via Peers for MSAE UI Configuration
ECA-9860 - Same MSAE policy UID is used for all machines
ECA-9862 - MSAE AD password is shown cleartext
ECA-9871 - Fix trace interceptor invocation duration
ECA-9872 - Regression: Peer publishing between 7.5 and older is broken
ECA-9873 - Error clicking "previous" CA certificate in CA structure certificate view
ECA-9877 - External RA: Unable to access external RA
ECA-9886 - Fix ACME pre-authorization order creation
ECA-9887 - Security Issue
ECA-9895 - Oauth login fails in chrome
ECA-9896 - Failed to get token from authorization server. HTTP status code 401
ECA-9900 - Fix AcmeConfiguration upgrade method.
ECA-9904 - LDAP Connection resets regularly
ECA-9908 - Test connection doesn't use the saved password
ECA-9909 - List of "Available MS Templates" isn't sorted
ECA-9912 - Incorrect table definition in sql script for MS-SQL for OcspResponseData.rowProtection
ECA-9916 - Implement oid claim for Azure
ECA-9919 - PKCS11HSMKeyTool fails with missing jna dependency
ECA-9924 - AD Search Scope too narrow
ECA-9931 - Security hardening
ECA-9932 - Fix exception with "default method" in Java on some environments
ECA-9933 - Must enter client secret again when saving OAuth provider
ECA-9938 - OAuth login in RA UI does not work over peer connection
ECA-9949 - OAuth: Failed to get token from authorization server.
ECA-9954 - Regression: NPE when getting non-existent configuration over peers, when debug logging is enabled
ECA-9956 - Conf files update is not reflected
ECA-9958 - Regression: NPEs on System Configuration page
ECA-9959 - MSAE SAN DNS Contains only domain part
ECA-9963 - EstRAModeBasicTest failing due to typo in expected error string
ECA-9967 - Errors in CA UI when TLS session is restarted
ECA-10042 - ACME EAB secret key logged on debug level