EJBCA 7.10.0.1 Release Notes
SEPTEMBER 2022
The EJBCA team is pleased to announce the release of EJBCA 7.10.0.1. (EJBCA 7.10.0 was an internal release, not generally available for customers).
This release includes REST API improvements, ECCDH support for key recovery, and certificate self-renewal among other features. The release also addresses several security issues.
Deployment options include EJBCA Hardware Appliance, EJBCA Software Appliance, and EJBCA Cloud.
Highlights
REST API Improvements
Expansion of the EJBCA REST API has been a top wish list item for some time and with this release, we have added new endpoints to make it easier to determine available profiles and manage CRLs. Several existing endpoints have also been improved to facilitate integration and you can expect further REST API expansion down the road.
New Endpoints
/v1/ca/{issuer_dn}/createcrl - CRL Creation
/v1/ca/{issuer_dn}/importcrl - CRL Import
v2/endentity/profiles/authorized/ - Retrieve end entity profiles the requesting client is authorized to. This allows clients to determine which profiles they can use for enrollment against the certificate REST API.
v2/certificate/profile/{certProfileName} - Retrieve certificate profile information, such as available key algorithms.
v2/endentity/profile/{profileName} - Retrieve end entity profile information, such as available certificate profiles and subject fields.
Endpoint Improvements
E-mail notification support for v1/endentity
Sort and pagination support for end entity search
Key specification parameters added to /v1/certificate/{request_id}/finalize. This allows for finalizing an approval request when the key algorithm is not already set.
For a full list of REST API fixes and improvements included in this release, see Issues Resolved in 7.10.
Documentation Improvements
Every EJBCA release comes with the bundled REST API documentation. In previous releases, the documentation for many endpoints was limited to endpoint URLs, request parameters, and response codes. In EJBCA 7.10, the documentation for all endpoints has been extended with more details including endpoint descriptions, parameter descriptions, and expected request and response values.
ECCDH Support for Key Recovery
We have added support for using EC keys to encrypt archived keys using ECCDH. For more information, see Encryption Keys in Key Recovery.
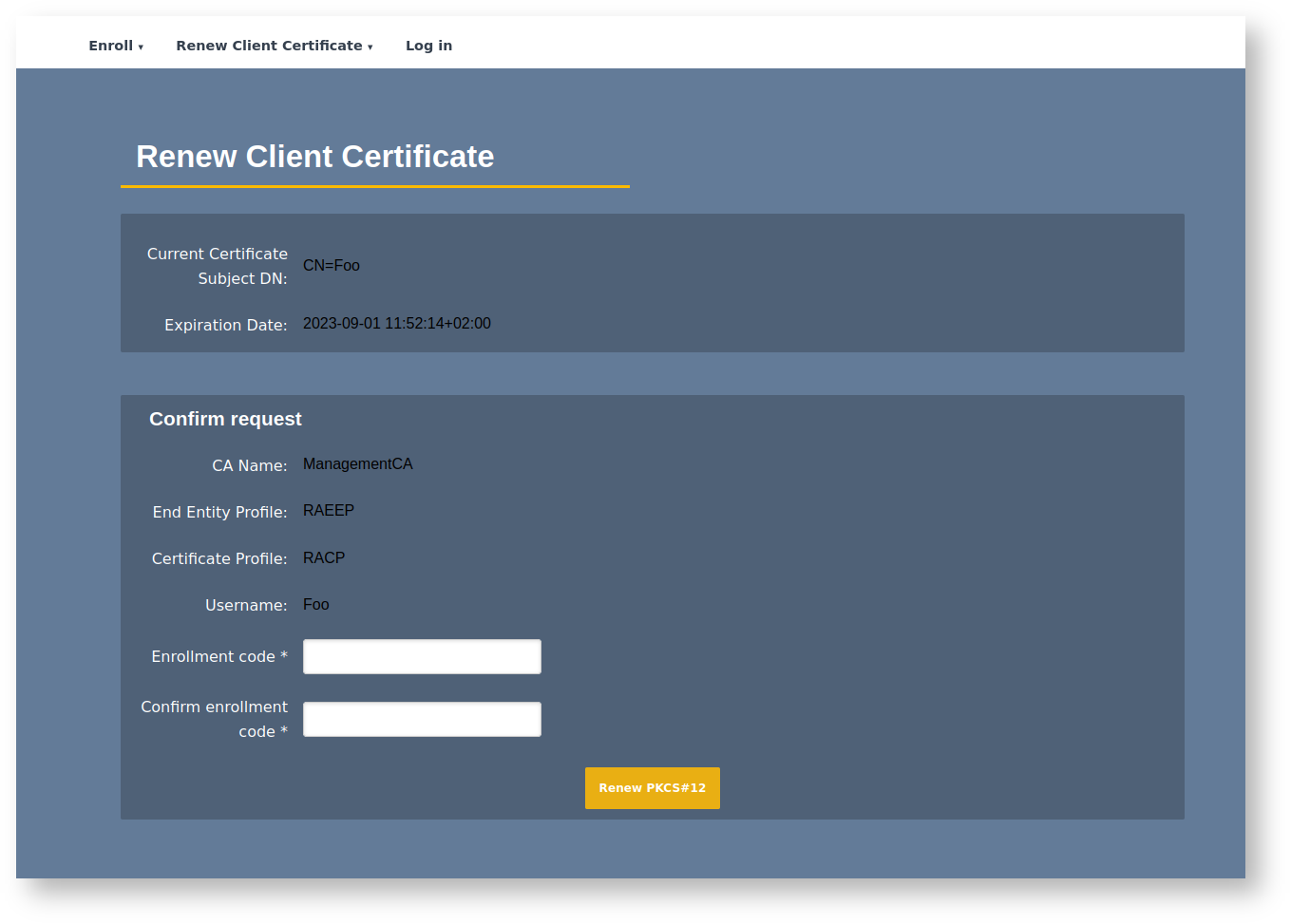
Certificate Self-Renewal
An updated version of the old self-renewal feature in the Public Web has been brought to the RA. Clients can now authenticate themselves to the RA Web using a client certificate and renew their own (and only their own) certificate without the intervention of an RA administrator. Administrators can enable this feature per end entity profile to specify a minimum amount of time before expiration that the renewal should be allowed. For more information, see the end entity profile field Allow Renewal Before Expiration, and to learn more about EJBCA RA operations, see the RA Operations Guide.
Security Issues
EJBCA 7.10 includes fixes for the following security issues.
Microsoft ADCS Vulnerability
Addressing a recent vulnerability discovered for Microsoft Certificate-Based Authentication, EJBCA now supports the new Extension szOID_NTDS_CA_SECURITY_EXT that maps the certificate to an Active Directory user/computer object. The extension will be allowed by default for all certificate profiles and included in certificates enrolled via EJBCA's Microsoft Auto-enrollment integration. For more information, see Microsoft ObjectSid Security Extension in Certificate Profile Fields.
XSS Vulnerability in CA UI
This release resolves a stored XSS vulnerability discovered in the EJBCA Admin Web. An authenticated administrator with sufficient access could compromise other administrators using the AdminWeb, via script injection. The injection could be done via addendentity.jsp for end entity profiles that have Number of allowed requests configured. Triggering occurred when viewendentity.jsp was rendered. An attacker would need administrator access, with access to the access rules /administrator, /ra_functionality/create_end_entity or /ra_functionality/edit_end_entity, and access to at least one End Entity Profile and at least one CA.
We r ate the issue as having high impact and medium probability. T his issue has been submitted as a CVE, see CVE-2022-39834.
XSS Vulnerability in RA Web
During internal testing, a stored XSS vulnerability was discovered in the RA Web end entity and certificate search pages, caused by subject fields not being escaped properly. This affects installations that allow subject fields to be specified by untrusted clients, for example, via protocols configured in RA mode, and profiles configured to allow subject DN override by CSR.
We r ate the issue as having medium impact and medium probability. T his issue has been submitted as a CVE, see CVE-2022-42954.
Upgrade Information
Review the EJBCA 7.10.0.1 Upgrade Notes for important information about this release. For upgrade instructions and information on upgrade paths, see Upgrading EJBCA.
EJBCA 7.10.0.1 is included in EJBCA Hardware Appliance 3.9.7, EJBCA Software Appliance 2.2.2 and EJBCA Cloud 2.11.0.
Change Log: Resolved Issues
For full details of fixed bugs and implemented features in EJBCA 7.10.0. and EJBCA 7.10.0.1, refer to our Jira issue tracker.
Issues Resolved in 7.10.0.1
Released September 2022
Improvements
ECA-10950 - ConfigurationHolder cannot expect that all external config files exists
Issues Resolved in 7.10.0
Internal Release September 2022
New Features
ECA-9266 - Create a REST call for retrieving an SSH CA's public key
ECA-9561 - ACME IP Identifier Validation http-01 Challenge
ECA-9998 - REST endentity/search call with pagination
ECA-10222 - Produce Pre-signed OCSP Responses Only for non-expired Certificates
ECA-10392 - Add REST end point to /ca to import a CRL
ECA-10574 - Allow v1/certificate REST module to be released with the next CE edition
ECA-10640 - Add HSM/PKCS11 support for CITS
ECA-10667 - CA type and CA Implementation for ProxyCA
ECA-10693 - Periodically update public keys on Azure OAuth Alias
ECA-10705 - Add 'Renew' to the menu and Implement the renew page UI
ECA-10706 - Implement the Renew Current Client Certificate section
ECA-10723 - Allow REST to use CSR + keep end entity email address
ECA-10742 - Sort and pagination on End Entity Search v2
ECA-10743 - REST Endpoint for CRL Creation
ECA-10765 - Add support for ssh-ed25519-cert-v01 for SSH keys/certificates
ECA-10795 - Make P11NG work with GCP KMS PKCS#11 library
ECA-10828 - Key encryption/archival using ECCDH
ECA-10868 - Remove default public access role after initial installation
ECA-10869 - REST Endpoint to get end entity profiles
ECA-10870 - REST Endpoint to get certificate profiles
ECA-10871 - REST Endpoint to get end entity profile content
ECA-10917 - Cert Safe Publisher in Community Edition
Improvements
ECA-10005 - App version, host and used auth is not shown when init wizard is
ECA-10009 - Remove old script based autoenrollment
ECA-10060 - Improve AcmeAuthorizationData data structure for read operations
ECA-10298 - Editing Certificate Extension Data in RA web
ECA-10386 - Keep Subject DN order in EE profiles with configdump export
ECA-10402 - Remove ejbca-setup.sh and modify documentation
ECA-10443 - ACME performance - Make challenge types configurable per ACME alias
ECA-10451 - Catch NPE for subject key ID in SearchCertificatesRestResponseConverterV2 REST API
ECA-10481 - Add protocol configuration to configdump
ECA-10519 - Add proper Git readme and license files in root directory
ECA-10562 - Add support for EE email in REST /v1/certificate/pkcs10enroll POST
ECA-10563 - Upgrade dnsjava to 3.5.0
ECA-10645 - Merge P11NG change to close sessions with unfinished operation
ECA-10649 - Upgrade json-smart to version 2.4.8 or later
ECA-10663 - Add Email notification support to /v1/endentity REST
ECA-10672 - Add internal "setupgradeversion" command
ECA-10677 - Create new access rule for restricted public access in RA UI
ECA-10679 - Migrate P11NG into its own module
ECA-10684 - Upgrade commons-codec to 1.15 or later
ECA-10687 - Upgrade commons-fileupload to 1.4 or later
ECA-10690 - Upgrade commons-text to 1.9
ECA-10697 - Upgrade Nimbus JOSE+JWT to nimbus-jose-jwt-9.21.jar
ECA-10700 - Upgrade csrfguard to 4.0.0 or later
ECA-10714 - Remove ROOT access requirement for EMPTY EEP when enrolling via Use Username
ECA-10720 - EJBCA REST API Update Time field doesn't work for query criteria with cert v2 api
ECA-10726 - Change ACME system test methods to challenge type to DNS to fix test failures in Jenkins
ECA-10727 - Replace cli-util with keyfactor-commons-cli
ECA-10733 - Remove references to ocsp.defaultresponder in ocsp.properties.sample
ECA-10739 - Allow renewal when certificate is about to expire
ECA-10741 - Implement EST enrolment (RE) for Proxy CA
ECA-10744 - Add keyAlg parameter to Finalize endpoint in certificate REST API
ECA-10746 - Improve ACME DNS challenge error handling and logging
ECA-10747 - In the renewal page, use client certificate from the request
ECA-10753 - Add index recommendation that plays nice with Keyfactor Gateway Connector
ECA-10762 - upgrade jakarta.activation to 2.1.0 or later
ECA-10773 - ConfigDump support for ProxyCA
ECA-10776 - Investigate and improve high db usage
ECA-10786 - Editing Certificate Other Data in RA web
ECA-10804 - Upgrade Extent libs
ECA-10805 - Upgrade csrfguard to 4.1.4 or later
ECA-10810 - Remove URLEncoder.encode-warnings from CaRestResourceSystemTest
ECA-10812 - Upgrade Apache Commons Configuration from 1.6 to 2.7
ECA-10815 - Remove src/pkg subdirectory
ECA-10817 - Include Domain FQDN for Kerberos / DC templates
ECA-10819 - Merge P11NG changes from SignServer
ECA-10821 - Documentation improvement for REST API
ECA-10842 - Wildfly 26 officially supported/recommended
ECA-10843 - clientToolBox: EjbcaWsRaCli stress: allow to specify the number of tests to run
ECA-10844 - clientToolBox: add a bit of tooling to help handling of the result.ser Serialized Java Object File
ECA-10909 - RA Web Self-Renewal improvements
ECA-10921 - Update Documentation on CA Fields with PrintableString encoding in DN
ECA-10932 - Improve post upgrade UI logging
Bug Fixes
ECA-2140 - Multichoice for SubjectDN fields generates Exception
ECA-4383 - Add input validation and remove case sensitivity from keybind modify command.
ECA-8929 - configdump can not import Super Administrator Role
ECA-9094 - Regression - Exception occurs in RA Web preferences on changing language
ECA-9169 - Issue in configdump import for CP with extended key usages.
ECA-10131 - Duplicate certificates when database.crlgenfetchordered is used
ECA-10300 - MSAE alias "Test connection" clears user input
ECA-10371 - Configdump does not differentiate between spaces and underscore and can miss items
ECA-10381 - Null Pointer Exception in eedetails.xhtml
ECA-10502 - Adding role member through RA web assert tokenIssuerId=0
ECA-10545 - RA Web Make New Request does not correctly parse CSR
ECA-10588 - Support OCSP Pre-Signer service in Configdump
ECA-10623 - Default CRL Distribution Point is not a valid URI when ( " ) is used
ECA-10639 - Duplicate OCSPKeyBinding Entry
ECA-10646 - CertificateCrlReader fails if full CA chain is not present on VA.
ECA-10660 - REST /v1/endentity/{user}/setstatus doesn't allow PEM token
ECA-10665 - IllegalStateException in End Entity view for superadmin
ECA-10675 - RA Request preview shows EKU even if cleared from Cert Profile
ECA-10692 - Intune revocation poller fails if CA uses ldap order
ECA-10703 - Improving the log entry when publishing CRL but not storing them in db
ECA-10707 - Improve EJBCA's behavior with trailing spaces
ECA-10711 - Email not displaying in waiting for approval status
ECA-10712 - Post Upgrade Failing
ECA-10713 - MSAE cannot be used if AD template has "Subject name format: None"
ECA-10715 - CAs list not correct in edit EE page in Ra
ECA-10725 - CSR parsing with -----BEGIN NEW CERTIFICATE REQUEST----- is missing
ECA-10730 - EJBCA ACME MOD_MD ISSUES (SSL.Com)
ECA-10731 - ACME email notifications - how to make it work
ECA-10734 - ADConnectionSingletonBean - could not obtain lock within 5000MILLISECONDS
ECA-10736 - No options for "Issuer" When Editing End Entity in RA Web if Available CAs is Set to “Any CA"
ECA-10745 - MSAE "RelatesTo" Id can get overwritten during parallel requests
ECA-10750 - MSAE does not work when EJBCA is running on Windows
ECA-10758 - Sun PKCS11 not working on RedHat OpenJDK 11.0.15
ECA-10763 - Name constraints throwing NPE after 7.6.0
ECA-10775 - getAvailableCAsInProfile(int entityProfileId) in Web Services does not return CAs in case Any CA
ECA-10779 - Community Edition build failures
ECA-10792 - Missing descriptions in swagger.json
ECA-10793 - Unable to enroll superadmin due to missing transactional support
ECA-10796 - fix clientToolBox help/documentation
ECA-10798 - REST protocols can't be enabled in CE
ECA-10801 - Unexpected Exception when creating new OcspKeyBinding (when not selecting Key Pair Alias)
ECA-10811 - CertificateCrlReader can't update certificate if type changes from standard to limited
ECA-10822 - JsfDynamicUiPsmFactory ArrayIndexOutOfBoundsException
ECA-10826 - Configdump EST configuration can not update
ECA-10827 - EST configuration in UI does not show most recent state
ECA-10830 - REST SSH resource improvements
ECA-10839 - RA web enroll make new request page does not properly handle required fields
ECA-10849 - SSH Rest access token and response content to UTF
ECA-10850 - Correct test failure Jenkins related to ticket eca 10775
ECA-10851 - Intune revocation only working with a proxy
ECA-10853 - Library load/activation failure of auto-activated PKCS#11 NG token causes partial lock-out from GUI
ECA-10856 - Address duplicate entries in NoconflictCertificateData table
ECA-10857 - AuthToken 250 character limit preventing certificate issuance
ECA-10860 - End entity DN merge does not work on fields with DN as attribute value
ECA-10864 - Issue on importing validators via configdump
ECA-10865 - Regression: Access rule with non-existent CA causes NPE on RA certificate search
ECA-10872 - Update ejbcaClientToolbox with log4j compatability flag
ECA-10875 - Regression: Upgrade to Commons Configuration 2 breaks database protection using HSMs
ECA-10876 - Error obfuscating non-ASCII passwords
ECA-10881 - Upgrade to Commons Configuration 2 reloads config every minute instead of at file change
ECA-10886 - Marker from REST resource is never removed
ECA-10890 - User needs to re-select algorithm after the certificate has been approved in RAWeb
ECA-10891 - Publish Queue Process Service does not handle missing certificate correctly
ECA-10894 - Configure Certificate Hash OCSP extension to always return if configured
ECA-10896 - Add CRL generation upon revocation is not working
ECA-10904 - Security Issue
ECA-10905 - Security Issue
ECA-10908 - Upgrade page in CA UI always show "Failed"
ECA-10920 - OCSP transaction and audit logging could not be modified in UI
ECA-10922 - Allow soft (default) key generation to support EdDSA
ECA-10923 - Missing libraries on p11ng-cli classpath causes NoClassDefFoundError for StringLookupFactory
ECA-10926 - Security Issue
ECA-10927 - NoClassDefFoundError for ejbcawsracli