SCEP Operations Guide
This describes operations using SCEP with EJBCA.
For an overview of EJBCA capabilities with SCEP, see the SCEP overview .
-
Related Content
Configuring SCEP
The SCEP URL is http://HOST:PORT/ejbca/publicweb/apply/scep/ALIAS/pkiclient.exe.
The URL contains a reference to a configuration alias 'ALIAS'. 'ALIAS' is an alphanumeric string that refers to the set of SCEP configurations that should be used when handling the SCEP request coming through this URL. It is possible to configure as many configuration aliases as desired using the command line or the CA UI.
Creating a SCEP alias with the name scep makes it available using the default URL (the same URL as in previous versions), http://HOST:PORT/ejbca/publicweb/apply/scep/pkiclient.exe.
Configuring SCEP in the CA UI
To configure SCEP using the CA UI, select System Configuration → SCEP Configuration.
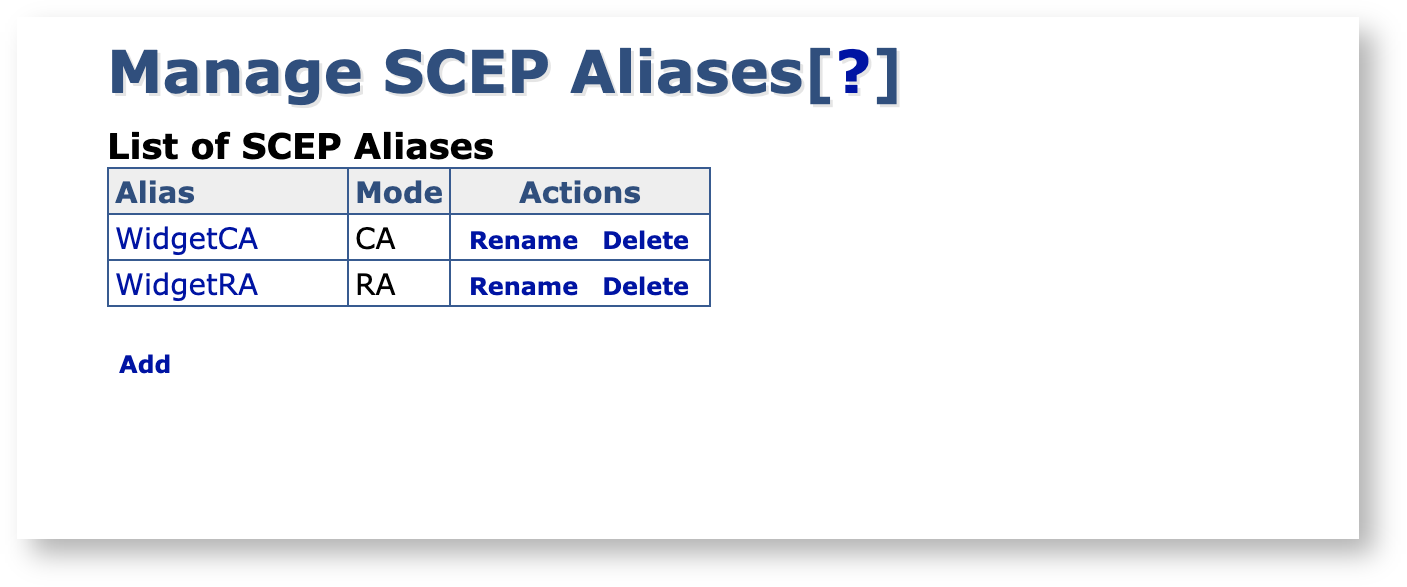
Note that you need /edit_systemconfiguration access to be able to edit the SCEP configuration. For more information, see Access Rules.
Configuring SCEP on the Command Line Interface
For information on creating and configuring the SCEP aliases using the command line, run the following command from the EJBCA home directory.
Creating a SCEP alias with the name scep makes it available using the default URL (the same URL as in previous versions), http://HOST:PORT/ejbca/publicweb/apply/scep/pkiclient.exe.
$ bin/ejbca.sh config scepAlias Properties
In CA Mode, EJBCA expects end entities to be manually created and for the SCEP client to merely enroll for certificates.
CA Mode

Properties
The following lists available properties.
|
Property |
Description |
|
Include CA certificate in response |
Set to true for the CA certificate to be transmitted back as a part of the response. |
|
Allow legacy digest algorithms in response |
Set to true to allow SHA1 and MD5 to be used in the response. If not set, defaults to SHA256. |
|
Allow Client Certificate Renewal (Enterprise Edition): |
Set to true in order to perform client certificate renewal, where an enrollment request which comes in at half the certificate's validity will automatically result in a new certificate being issued. |
|
Allow Client Certificate Renewal using old key (Enterprise Edition): |
Set to true in order to allow client certificate renewal to be performed on existing keys. |
RA Mode
ENTERPRISE This is an EJBCA Enterprise feature.
In RA Mode, EJBCA does not require the end entity to be enrolled but will instead create it as a part of the issuance process.
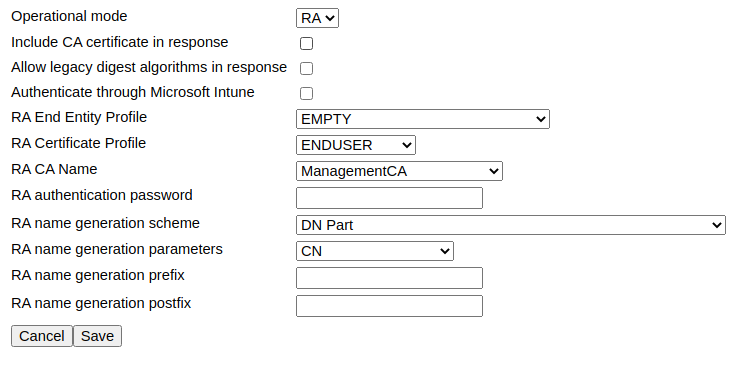
Properties
The following lists available properties.
|
Property |
Description |
|
Include CA certificate in response |
Set to true for the CA certificate to be transmitted back as a part of the response. |
|
Allow legacy digest algorithms in response |
Set to true to allow SHA1 and MD5 to be used in responses. If not set, defaults to SHA256. |
|
Authenticate through Microsoft Intune |
Validates SCEP requests with Microsoft Intune, see RA Mode with Microsoft Intune Support. |
|
RA End Entity Profile |
The end entity profile to use for the enrolled end entity. |
|
RA Certificate Profile |
The certificate profile to use for the enrolled end entity. |
|
RA CA Name |
The CA to enroll the end entity under. |
|
RA authentication password |
An authentication password to require in the request. |
|
RA name generation scheme |
How to generate the end entity username. |
|
RA name generation parameters |
What to base the end entity username off of. It can be a part of the DN, the complete Subject DN, randomized or fixed. |
|
RA name generation prefix |
A general prefix to prepend on end entity usernames. |
|
RA name generation postfix |
A general postfix to append on end entity usernames. |
RA Mode with Microsoft Intune Support
ENTERPRISE This is an EJBCA Enterprise feature.
While in RA Mode, EJBCA can also use Microsoft Intune to validate SCEP requests. Enabling the option Authenticate through Microsoft Intune adds Intune specific configuration properties. As you can see in the example configuration below, selecting to authenticate through Intune disables the RA authentication password field, since the password is checked with Intune instead.
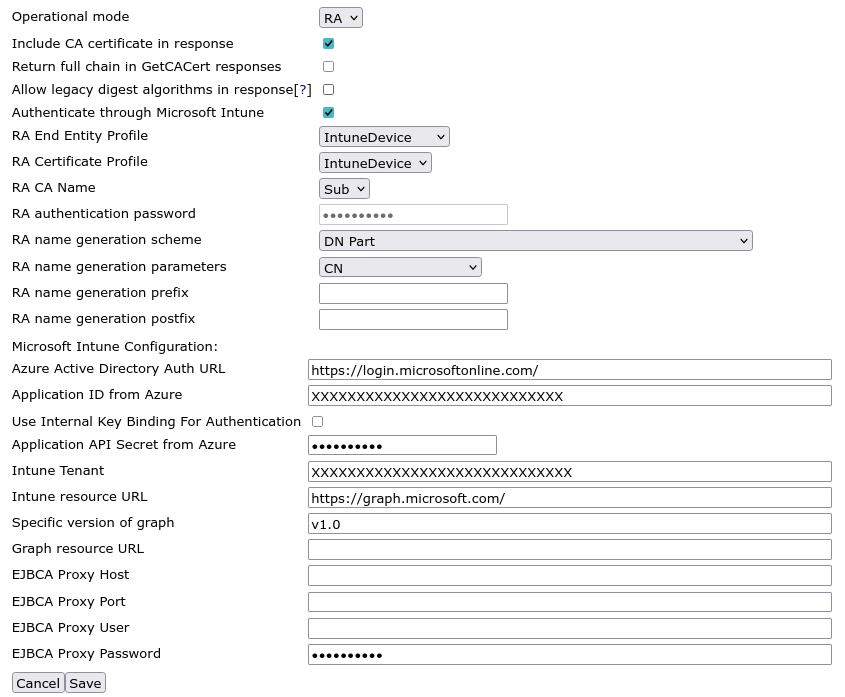
Properties
|
Name |
Description |
|
Azure Active Directory Auth URL |
Azure Active Directory Authentication URL is for issuing the login token. This value must be specified if using EJBCA in another Azure cloud such as US Federal or another region. If no value is specified the default value is used: https://login.microsoftonline.com/
|
|
Application ID from Azure |
Application ID obtained by creating a new Application Registration. See Configure Intune for steps to obtain the Application ID. |
|
Application API Secret from Azure |
API secret obtained by creating a secret in the application that was registered. See Configure Intune for steps to obtain the API secret.
|
|
Intune Tenant |
The Intune Tenant is the domain name of the user account used to login to Microsoft Azure. If the account domain name is admin@primekey.com the Intune tenant would be primekey.com. |
|
Intune resource URL |
This is used to specify the token audience in Azure. This value must be specified if using EJBCA in another Azure cloud such as US Federal or another region. If no value is specified the default value is used: https://api.manage.microsoft.com/
|
|
Specific version of graph |
The version of the Microsoft Graph API. This value defaults to version 1.0 if the value is not specified. |
|
Graph resource URL |
The URL to specify auto discovery for Intune. This value must be specified if using EJBCA in another Azure cloud such as US Federal or another region. If no value is specified, the default value is used: https://graph.windows.net/
|
|
EJBCA Proxy Host |
The host that the proxy is hosted on that clients point to for Internet access. |
|
EJBCA Proxy Port |
The port number of the proxy that clients point to for Internet access. |
|
EJBCA Proxy User |
The username of the account used to login to the proxy if the proxy is configured for basic authentication. |
|
EJBCA Proxy Password |
The password of the account used to login to the proxy if the proxy is configured for basic authentication. |
Sample Client Messages
While many SCEP clients exist (as listed on the SCEP overview page), many use cases require writing custom clients. Using the BouncyCastle crypto libraries, we've produced some sample implementations in Java if you need some help in getting going. For more information, see SCEP Client Support.