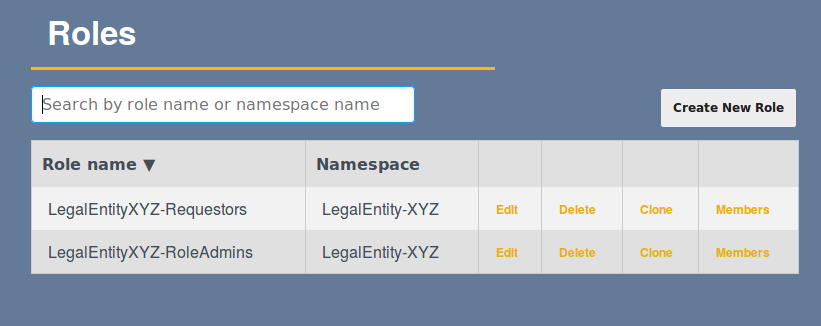
Managing Role Namespaces
This covers managing Namespaces on the Role Management page and describes a typical process when using Namespaces.
For information on the general concepts of roles and access rules, see Roles and Access Rules.
Managing Namespaces
Using the role management pages, the desired namespace to be associated with the role may be selected, or a new namespace created.
Using Namespaces
A typical process when using Namespaces is to have two organization, OrganizationA and OrganizationB that can:
register end entities for profiles related to the respective organization
issue certificates for these end entities, from IssuingCA (note that the same CA is used for both OrganizationA and OrganizationB)
an Organization administrator can add new role members to perform these tasks for the Organization
an Organization administrator can add new roles with less or the same privileges as his own role
A process to configure the above is:
Create profiles and roles for OrganizationA
Create certificate and end entity profiles to issue the desired certificates for OrganizationA, from IssuingCA
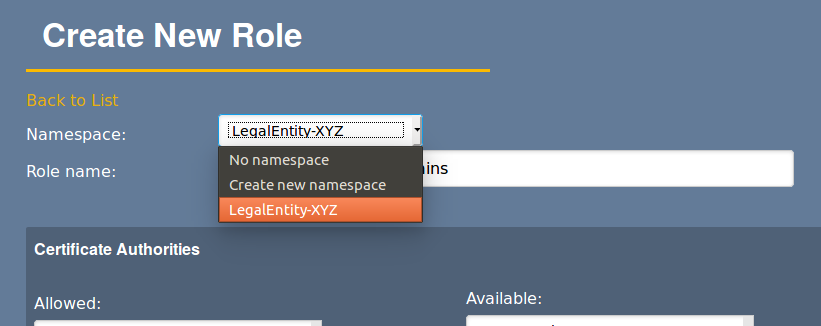
Create a role for RA Admins for OrganizationA, adding a Namespace for this role called OrganizationA
Configure the role with access to IssuingCA and the end entity profile, i.e. everything needed to issue the certificates the RA Admins should issue
Clone the RA Admins role into a Role Admins role for OrganizationA, selecting the namespace OrganizationA
The Role Admins role need the same privileges as the RA Admins role, because Role Admins can not manage roles that have more privileges than their own role
Add roles needed to manage roles, using Advanced mode in Admin UI→Roles and Access Rules:
/system_functionality/edit_administrator_privileges/
/system_functionality/view_administrator_privileges/
/ca_functionality/view_ca/
/ca_functionality/view_certificate/
/ca/<CA issuing admin certificates>/
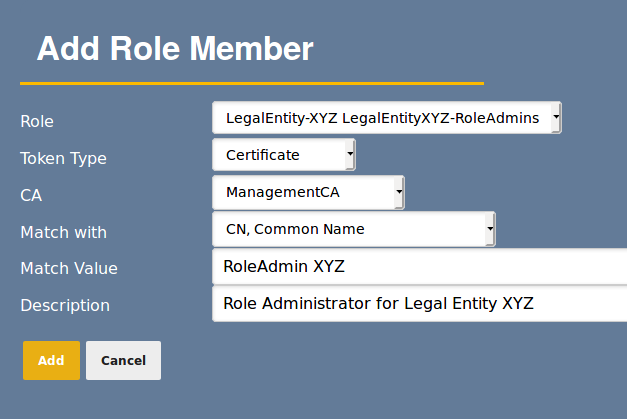
Assign members to the RA Admins and Role Admins roles for Organization A
Create profiles and roles for OrganizationB
Clone the certificate and end entity profiles to issue the desired certificates for OrganizationB, from IssuingCA, with any profiles changes related to OrganizationB
Clone the role for Role Admins, adding a Namespace for this role called OrganizationB
Edit the role with access to add new role members to this role
Clone the role for RA Admins for Organization B in to a Role Admins role for OrganizationB, as done for OrganizationA above
Assign members to the RA Admins and Role Admins roles for Organization B
Now Role Admins for OrganizationA that logs in, will only see the roles within the namespace OrganizationA, and vice versa for Role Admins in OrganizationB.
Now RA Admins for OrganizationA that logs in, will be able to issue certificates using end entity and certificate profiles configured for OrganizationA, through access rules in the role, and vice versa for RA Admins in OrganizationB.
Role and RA administrators can only perform their tasks in the RA UI, unless they have the access rule /administrator/ in their respective roles.