External OCSP Responders
Externalizing your OCSP service to a Validation Authority provides several benefits:
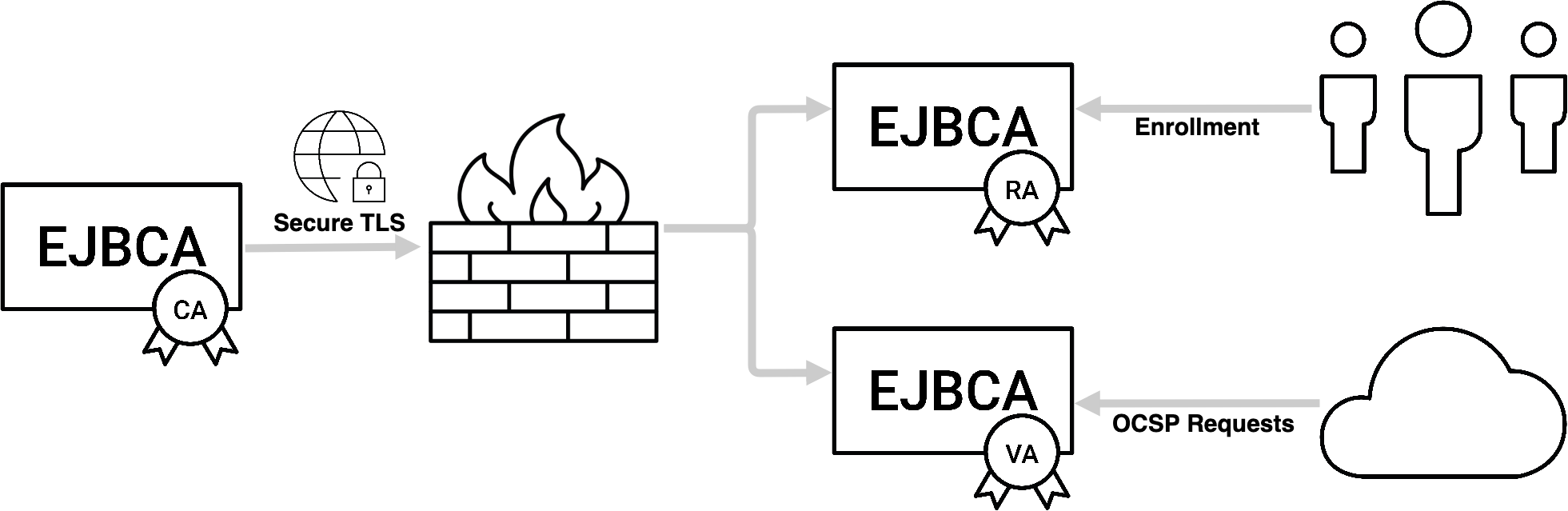
By separating the validation service from the CA, security is increased by allowing the CA to reside behind a firewall not allowing incoming connections, while the VA(s) reside in the DMZ.
Externalization of the VA allows for greater degrees of availability. Separation allows for maintenance to be performed on even unclustered CAs without any downtime on OCSP services.
Ensure the highest performance. Even though the OCSP responder is fast, it's not uncommon for loads on a VA infrastructure to be extremely high at times. Several VA nodes can set up to proxy for the same CA behind a load balancer, and VA nodes can be localized geographically to ensure minimal RTT.
The following shows a rough schema of the architecture using external OCSP responders.
Features
Independent of CA software used (various degrees of integration possible and may be required).
One responder can respond for any number of CAs.
Status information stored in SQL database.
Not depending on CRLs. Status information can be updated in real-time.
Plug-in mechanism for custom OCSP extensions.
Highly configurable audit and transaction logging. Suitable for invoicing.
Supports PKCS#11 HSMs and soft keys.
Built-in health check used by load balancers and for monitoring.
Configurable for requiring signed requests, authorized signers, etc.
Can answer good or unknown to non-existing certificates, with different configuration based on request URI.
Linear scalability for performance and high availability by adding multiple nodes.
High performance, >500 requests per second on a single server.
On-line renewal of OCSP responder keys and certificates.
OCSP client in Java (Client ToolBox).
Support for Norwegian Unid FNR extension.
Support for German CertificateHash extension.